Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve Matrix machine.
Description
Matrix is a medium level boot2root challenge. The OVA has been tested on both VMware and Virtual Box.
Difficulty: Intermediate
Flags: Your Goal is to get root and read /root/flag.txt
Networking: DHCP: Enabled IP Address: Automatically assigned
Hint: Follow your intuitions … and enumerate!
For any questions, feel free to contact me on Twitter: @unknowndevice64
Information gathering
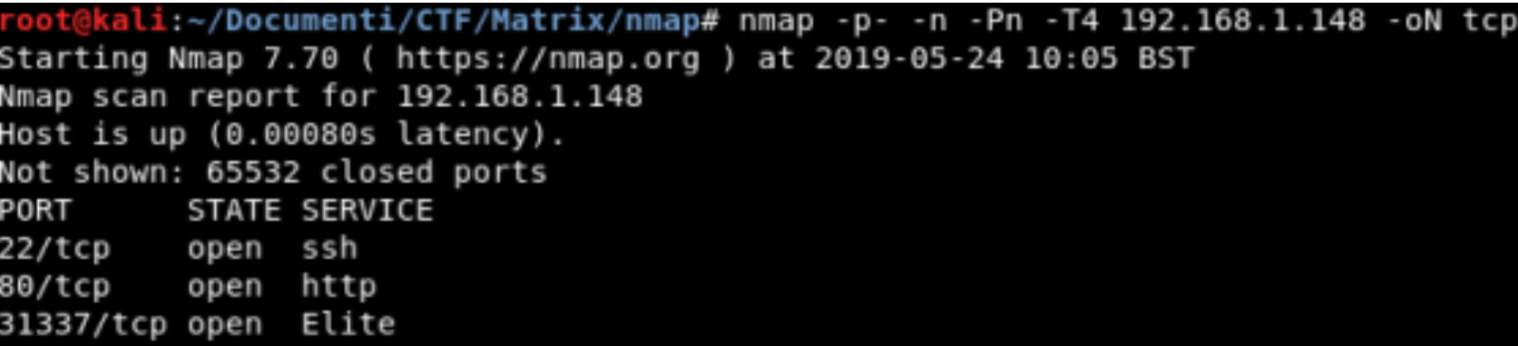
TCP Scanning
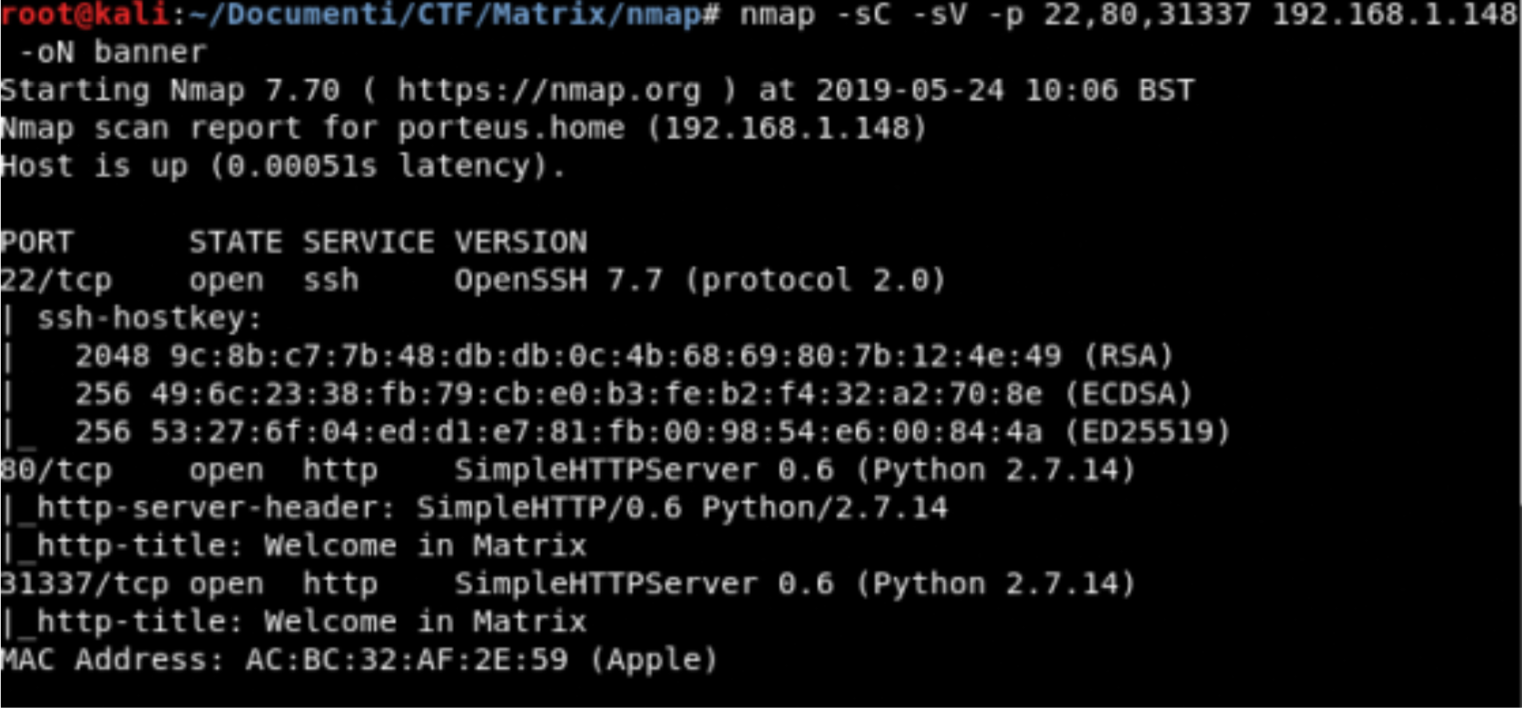
Banner Grabbing
HTTP
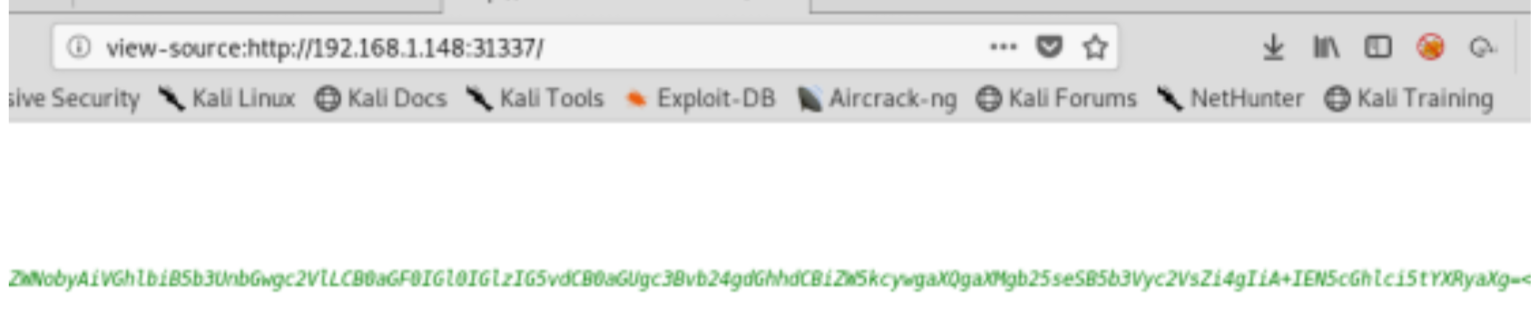
Checking the source code of the home page (Port 31337) we can find a string coded in base64
Decode base64 string
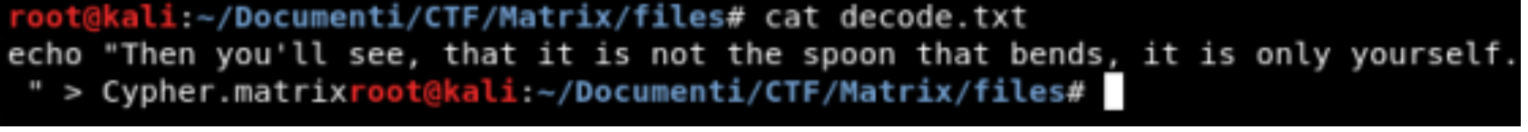
Decoded text
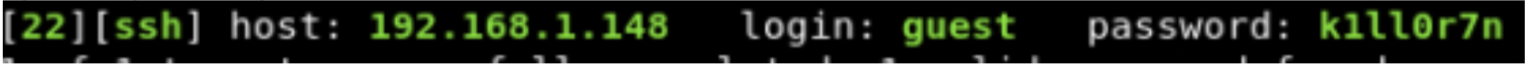
You can enter into matrix as guest, with password k1ll0rXX
Note: Actually, I forget last two characters so I have replaced with XX try your luck and find correct string of password
Fantastic we can access to the machine as a guest, but unfortunately, the password is not complete.
Crunch
We can use crunch to generate the passwords:
Unfortunately, we have a restricted shell, so the next step is to escape it 😛